Level Up with Agentic AI
DruAI has evolved into fully agentic AI, built to help IT, Security, and Compliance teams move from answers to outcomes.
One Tool, Limitless Possibilities
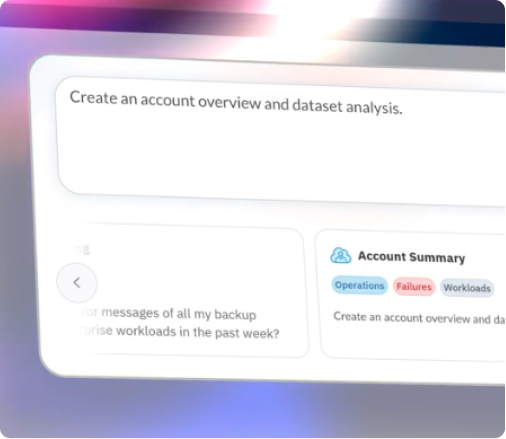
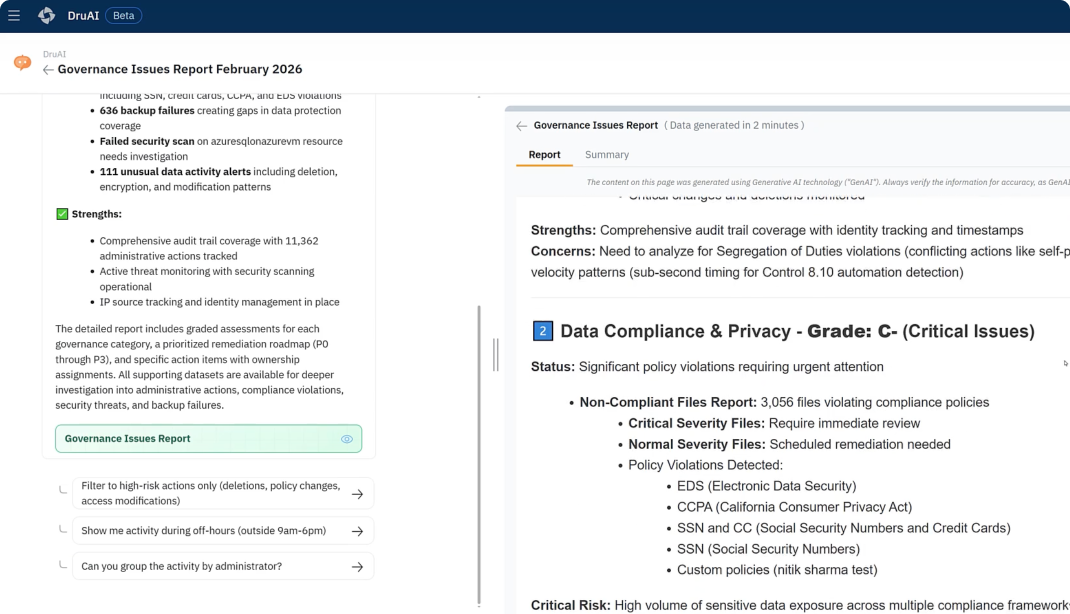
Dru brings backup intelligence to the surface through a guided, conversational experience, so teams can understand what’s happening, interpret signals, and decide what to do next without digging through logs or opening a ticket.
Agentic Data Security is Here
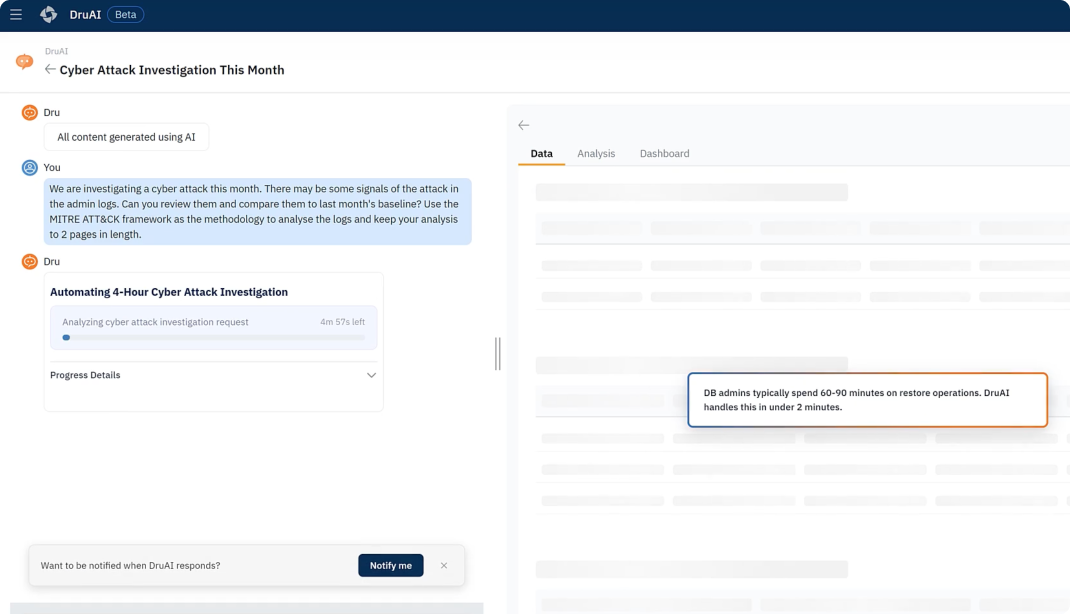
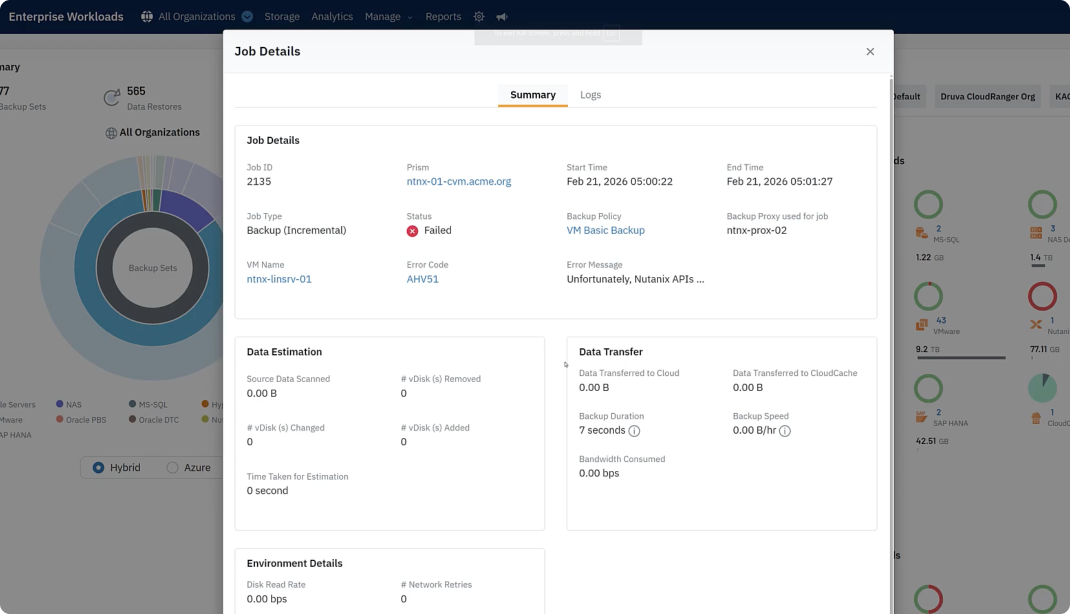
Let Dru do it for you! Leverage agentic AI to explore backup health and trends, accelerate troubleshooting with in-product expertise, and enhance threat investigation with targeted searches.
Dru Agents
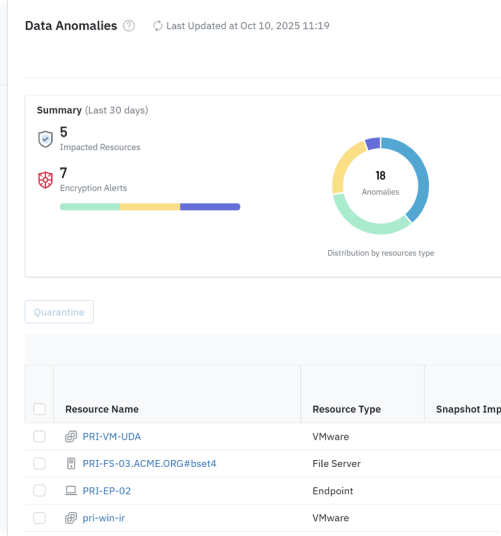
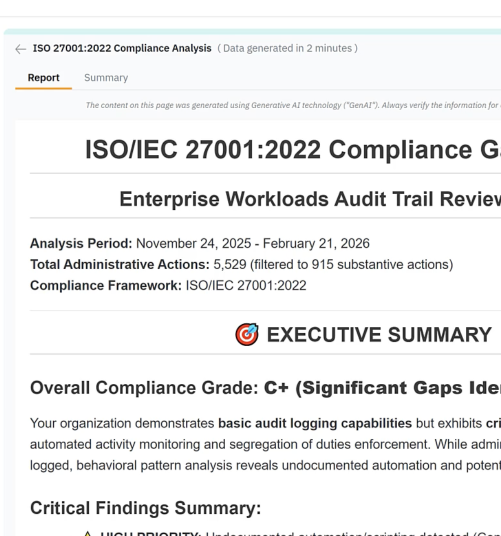
Agentic AI interprets intent, analyzes signals for trends and risks, guides troubleshooting and investigation, automates tasks like recovery and policy creation, and distills complex information into actionable insights and visualizations.
Dru MetaGraph
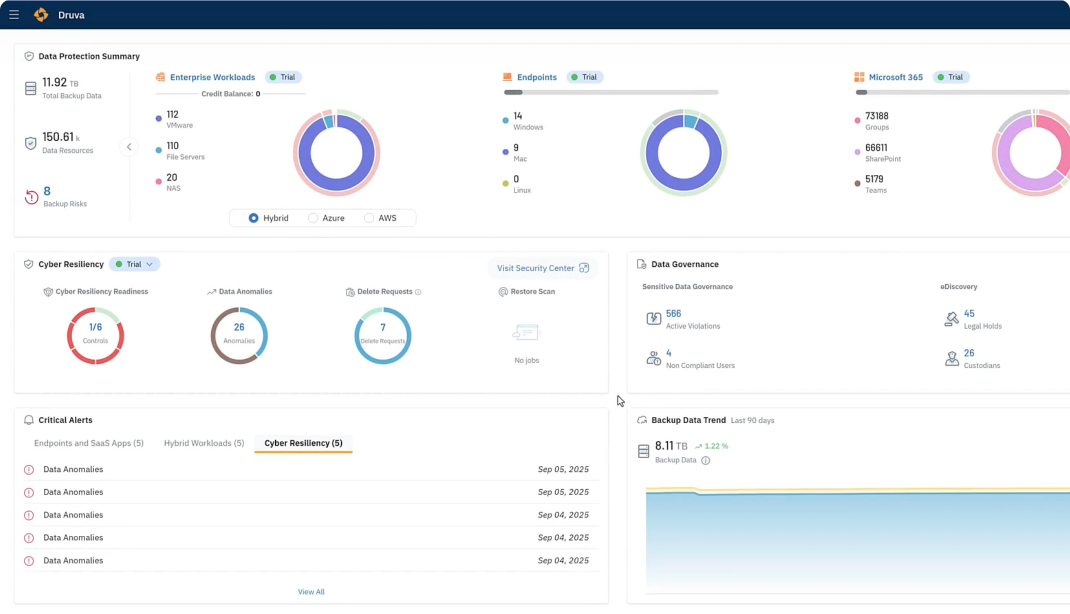
Tenant-specific, graph-powered foundation for real-time data intelligence, including permissions, identity, activity, configuration, events, and context. This information enables Dru to respond smarter to user needs, answering questions in real time, and guiding (or automating) the next best action.
Dru Assist
AI-powered support experience offering 24/7 self-service for instant answers, guided troubleshooting, and access to knowledge resources. Users get instant setup and configuration, contextual in-product guidance, and a seamless escalation path to live chat with expert support when necessary.