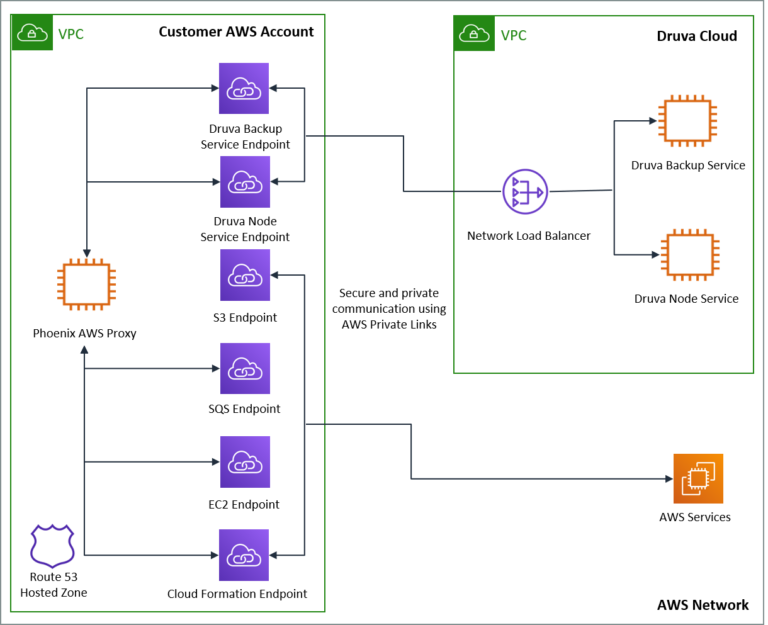
We are happy to announce that Druva Phoenix now supports AWS PrivateLink for its cloud-based disaster recovery-as-a-service (DRaaS) solution. Druva is the first SaaS data protection vendor to leverage AWS PrivateLink. This means communication between customer AWS accounts and Druva services now occurs through AWS PrivateLink, ensuring that network traffic always stays securely within the AWS network and traffic is never exposed to the public internet. Druva also automates the entire DRaaS configuration with AWS PrivateLink and customers can now use a one-click process to deploy CF templates, deploying the entire configuration infrastructure within the customer’s AWS account. This enhancement is included with all tiers of service.
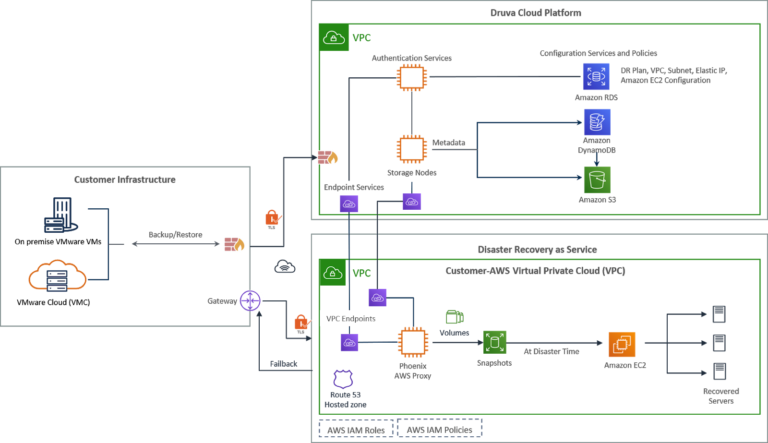
Druva’s DRaaS functionality extends its cloud data protection solution for enterprise infrastructure by enabling customers to failover backups of VMware virtual machines (VMs) from the Druva Cloud into their AWS virtual private cloud (VPC). In case of a disaster or similar high-stakes event, this capability ensures business continuity without the need for additional dedicated on-premise software, storage, or hardware, helping to reduce costs and improve agility. VMs are recovered on-demand in the cloud in minutes (typically less than 30 minutes).
What is AWS PrivateLink?
AWS PrivateLink provides a private connectivity between VPCs and services hosted on AWS or on-premises, securely on the Amazon network. By providing a private endpoint to access your services, AWS PrivateLink ensures your traffic is not exposed to the public internet. AWS PrivateLink makes it easy to connect services across different accounts and VPCs to significantly simplify your network architecture in addition to the following key benefits:
- Fast and secure data transfer over AWS prevents use of public internet
- Simplifies network configurations
- Uses private IP addresses
Integrating PrivateLink with Druva Phoenix
The following diagram shows an overview of the Druva Phoenix architecture, including its security capabilities and the implementation of AWS PrivateLink.