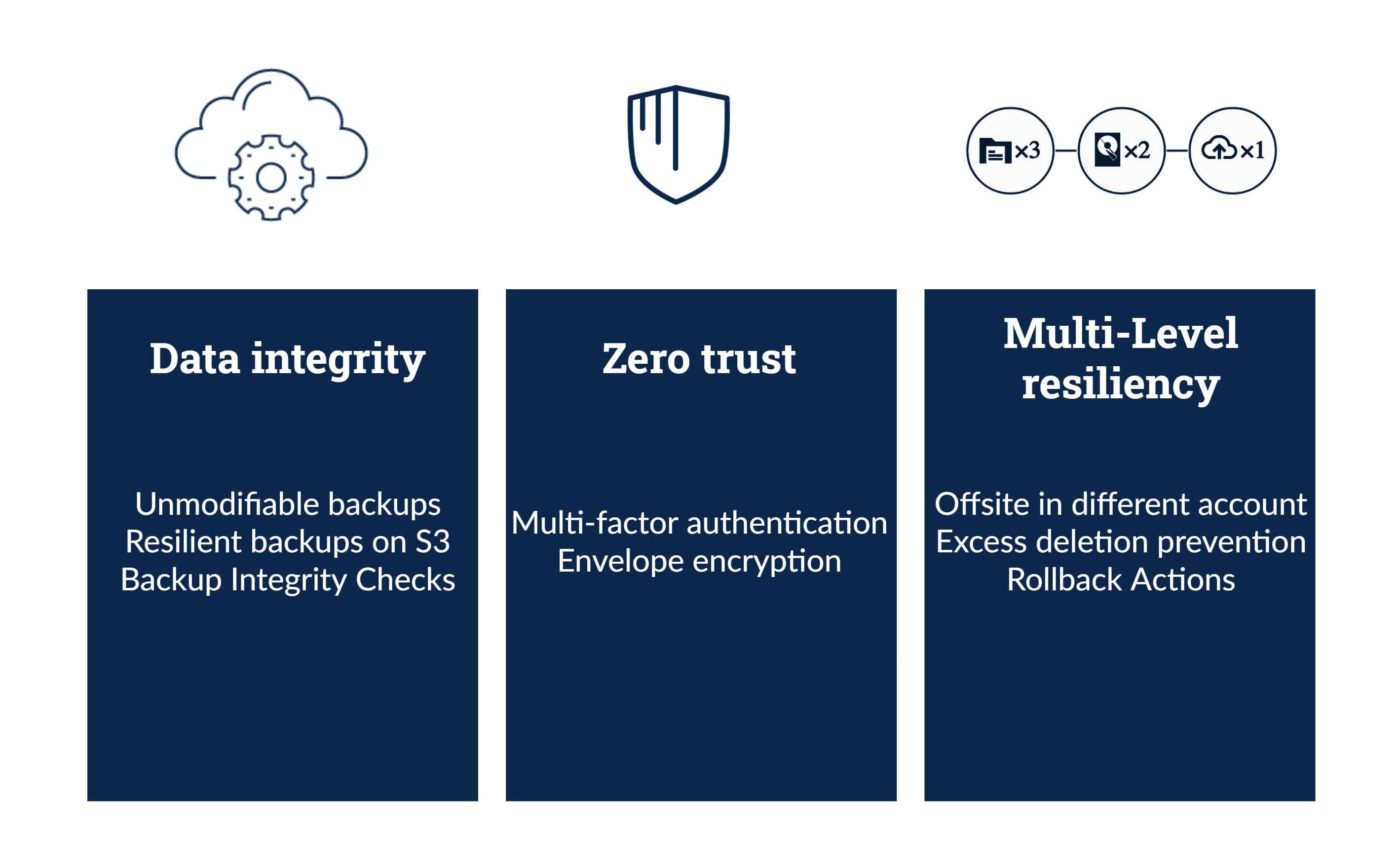
Druva meets both operational security and data integrity by being a SaaS-based backup solution offering customers the best in robust data integrity, data availability, operational security, and accelerated recovery.
- Each cloud-based backup is air-gapped and safe from malicious software execution.
- There is no access to backups, so ransomware can’t encrypt or delete.
- The Druva Data Resiliency Cloud has a robust security model in place with continuous scanning, patching, upgrades, and is housed on the global AWS secure platform for additional security and durability.
- The Druva Data Resiliency Cloud has full workflows for recovery in any situation.
But what about bad actors you say? Ransomware usually gets the news headlines, but what if a malicious insider has full access to your multi-cloud, and even backup environments? What about an angry or disgruntled administrator? Or, what if there’s just an accidental data issue? If someone has full access to your cloud and is able to circumvent or verify the full MFA policies put in place, all it takes is a deliberate or accidental deletion to ruin your chances of recovery.
Now that I’ve added additional stress to your security posture, how do we solve this? Well…
Continuous monitoring and rollback actions
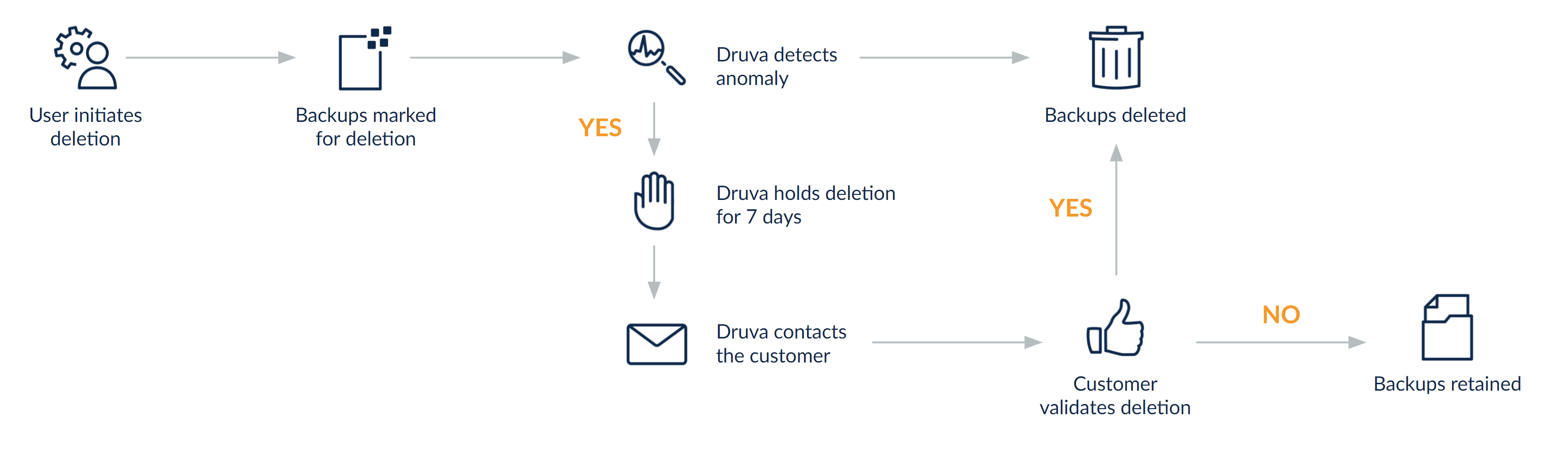
The Druva Data Resiliency Cloud has many benefits over any classic “maintain it yourself” backup solution. But, the two we are going to focus on are Continuous Monitoring and Rollback Actions. As part of the Druva solution, our amazing 24x7x365 Cloud and Security Operations team monitors backup environment actions, and uses anomalous detection algorithms to alert us when something seems off. We aren’t just monitoring the success or failure of your backups to let you know there might be a problem, and while we don’t ever touch the backups themselves, we are also monitoring back-end data about your account and environment.
For example, someone deleted 100 users on a Monday morning and that’s never happened before? That’s a little odd, let’s reach out to you. Entire backup sets are deleted or entire swaths of devices are removed. Are you decommissioning servers? Do you need to retain that? That’s a little odd so let’s reach out. Someone who has never logged in from another country all of a sudden seems to be deleting everything you have, we should probably give you a call.
But notification and continuous monitoring are only a part of it. It does you no good if we call you and tell you that all of your backups were deleted only to find out you didn’t initiate it, so the other aspect to this is rollback actions.
Rollback actions are like a secondary safety net in the “air-gapped” aspect of your backup strategy. Within the Druva Data Resiliency Cloud, even if you are deleting objects, users, or backups, we still maintain them for several days afterward just in case. Think of it as analogous to a recycle bin. But this bin can’t be emptied by the customer or a bad actor. So if you accidentally delete the wrong laptop device and realize it after the fact, or someone goes in and starts removing users and profiles — don’t worry, we still have them and they are safe. In the case of credential misuse where a bad actor may maliciously remove endpoints, users, virtual machines, NAS or file shares, or even databases, the rollback actions feature will keep track of these and allow administrators to quickly recover not only the data from deleted backups but also environmental objects as well. This provides the administrator the ability to revert malicious or unintended actions without any loss of data, and enables the restoration of productivity rapidly.
So how does this process work? With billions of backups, of course we aren’t calling everyone every time a single device is deleted — we rely on advanced detection and alerting based on aberrant behavior. So what if, all of a sudden, we start to see hundreds or thousands of deletions? This will trigger our AI-enabled anomaly detection engine, flagging an alert to our SecOps and support team. This would then typically result in a support engineer reaching out to you to ask what’s going on.