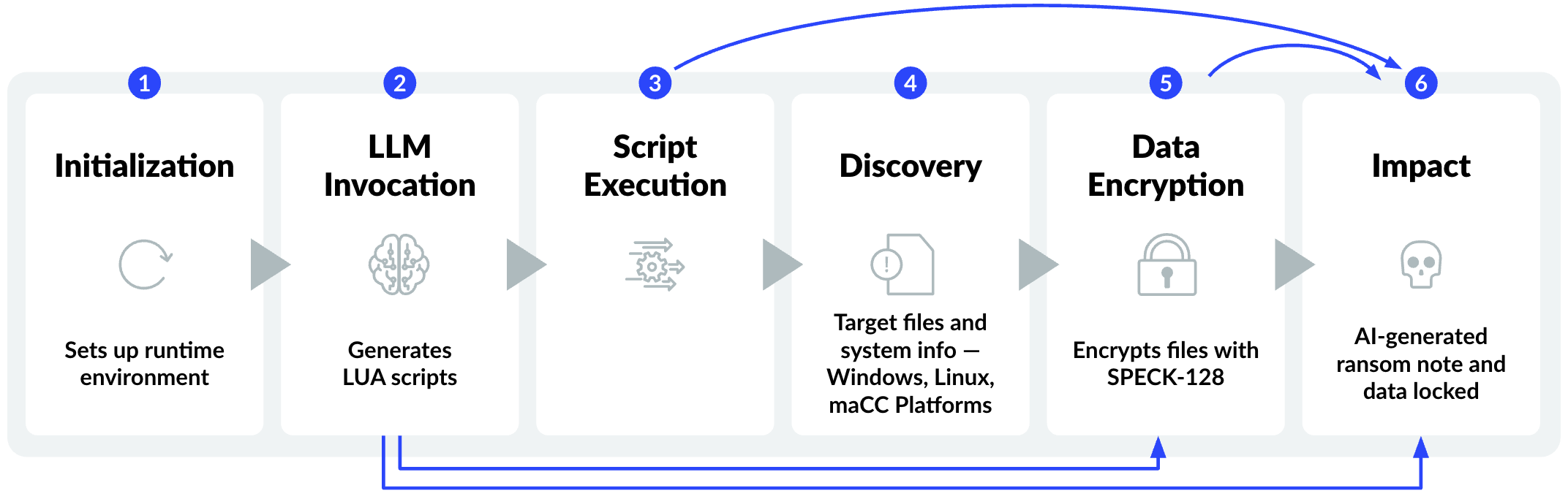
How PromptLock Works: Dynamic AI-Powered Attack Chain
Initialization
LLM Invocation
Script Execution
Key Management & Encryption
main_generateRandomKeyHex → Generates random key in hex.
main_hexkeyToLuaWords → Prepares the key for use in Lua.
Implements SPECK-128 .Files are encrypted in 16-byte blocks and overwritten.
Auxiliary Functions
Cross-Platform Lua Payloads
Lua scripts allow execution across Windows, Linux, and macOS, giving PromptLock broad reach without platform-specific payloads.
Artifacts and File Traces
scan.log → File inventory
target_file_list.log → Candidate files
payloads.txt → Staging data
Ransom Note
AI-generated ransom notes include a Bitcoin address historically tied to Satoshi Nakamoto, used for psychological manipulation rather than real payment collection.
Indicators of Compromise (IOCs)
SHA-256 Samples:
MITRE ATT&CK Mapping
Tactic
| Technique
| Details in PromptLock
|
Execution
| T1059.007 (Command and Scripting Interpreter: Lua)
| main_execLua runs AI-generated Lua scripts.
|
Execution
| T1647 (AI-Generated Code) *
| main_invokeLLM queries Ollama for dynamic script generation. (proposed emerging technique)
|
Discovery
| T1083 (File and Directory Discovery)
| Lua tasks enumerate files, logged in scan.log.
|
Collection
| T1119 (Automated Collection)
| AI scripts select and stage target files in target_file_list.log.
|
Exfiltration
| T1041 (Exfiltration Over C2 Channel)
| Lua tasks can exfiltrate via generated instructions (observed in analysis).
|
Impact
| T1486 (Data Encrypted for Impact)
| Files encrypted with SPECK-128, overwritten in place.
|
Impact
| T1491.001 (Defacement: Internal Defacement)
| AI-generated ransom note dropped with Bitcoin address.
|
Defensive Takeaways
Detect Ollama misuse: Monitor access to localhost:11434.
Lua anomaly detection: Flag unusual use of embedded Lua interpreters.
Behavioral ransomware hunting: Look for rapid block overwrites and log file creation.
Restrict local AI runtimes: Confine Ollama to dev-only environments
PromptLock represents the first AI-powered ransomware PoC, showing how LLMs can dynamically generate malicious logic at runtime. While still experimental, it is a warning sign: AI is lowering the barrier to entry for advanced ransomware.
How Druva Can Help
While your primary security tools provide best-in-class threat prevention, detection & response, Druva provides the last line of defense for when sophisticated threats like PromptLock get through and you do need to get back to normal. Follow these steps:
1. Implement an Incident Response Plan
Review and test your incident response plan in a timely manner to ensure you can effectively respond to a potential breach, including utilizing Druva's recovery capabilities.
Security Command Center
Periodically monitor security posture of your Druva environment (for Data Anomaly alerts, Threats, Access Risks, New geolocation events) etc. and take swift action.
Data Anomaly Detection Alerts
Proactively identify data anomalies across Endpoints, NAS, File Servers, VMware, Microsoft OneDrive and SharePoint data.
Monitor alerts for mass creation, modification, encryption, and deletion actions across all resource types.
Subscribe to the Data Anomaly Alerts report and related alerts to receive timely notifications via email.
Leverage Threat Hunting
Druva’s IOC Library is always up to date with the latest threat intel. Investigate IOCs by performing periodic threat scans on your AWS EC2, VMware VM, and Azure VM backups to ensure their integrity. IOCs specific to PromptLock have been published by Druva’s in-house threat research team and can be found in the IOC Library.
Utilize Federated Search to scan for IOC SHA values across your backed-up data (Endpoints, Microsoft 365, Google Workspace, etc.) to detect threats. Immediately quarantine detected infections via Federated Search to contain them, or use Defensible Delete to remove them from both the backup snapshot and the source.
Quarantine Backups
Cyber Recovery: Leverage Druva’s cyber recovery workflows to ensure clean, lossless recovery
How resilient are you against ransomware like PrompLock? In just 5 minutes, benchmark your cyber resilience, uncover hidden security gaps, and get a personalized score you can act on. Assess your cyber resilience now.