As enterprise IT environments evolve, backups are no longer the final line of defense — they're a crucial part of the cybersecurity strategy. With the rising sophistication of ransomware attacks and data breaches, organizations face growing challenges in ensuring their backups are not only available but also uncompromised and secure. Recovering from backups isn’t just about access anymore; it’s about ensuring data integrity, maintaining customer trust, and doing it all at the speed modern businesses demand.
Druva’s Recovery Intelligence directly integrates threat intelligence and security context into the recovery workflow. By surfacing real-time indicators like anomalies, encryption, malware presence, and antivirus scan results, it helps enterprise customers make fast, confident decisions during recovery.
In this blog, we’ll explore how Recovery Intelligence helps you assess restore points across your cloud backups and build a more secure, automated cyber recovery strategy — without adding operational overhead.
Why Recovery Context Matters
Traditional backup systems were designed to answer one question:
“Can I restore my data?”
Today, the question is more nuanced:
“Can I safely restore this data without reintroducing risk?”
Modern threats like ransomware, prolonged malware dwell time, and insider threats mean that restore points must be verified not just for availability, but also for security. Restoring a system from an infected backup risks reinfection, creating a cycle of recovery failures and wasted time.
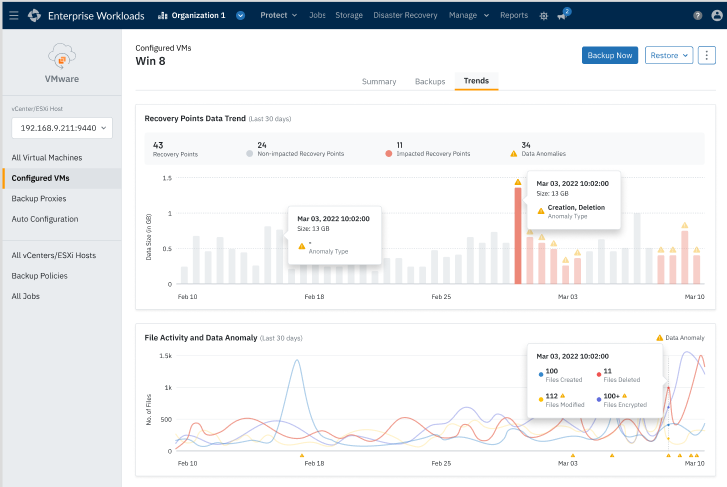
This is where Recovery Intelligence steps in. By utilizing advanced Recovery Intelligence, organizations can identify and isolate infected snapshots before they are restored, minimizing the risk of reinfection. With actionable insights, you can quickly pinpoint safe recovery points, reducing the time and complexity needed to return your systems to a clean, operational state.
Recovery Intelligence streamlines the entire recovery process, enabling you to act with confidence even in the face of sophisticated threats. Whether dealing with ransomware or hidden malware, Recovery Intelligence ensures your restores are secure, clean, and efficient. As ransomware raises the stakes, this level of assurance isn’t just helpful — it’s essential.
What is Druva Recovery Intelligence?
Recovery Intelligence is a capability within Druva's Data Security Cloud that provides real-time, recovery-focused visibility through the following existing cyber components:
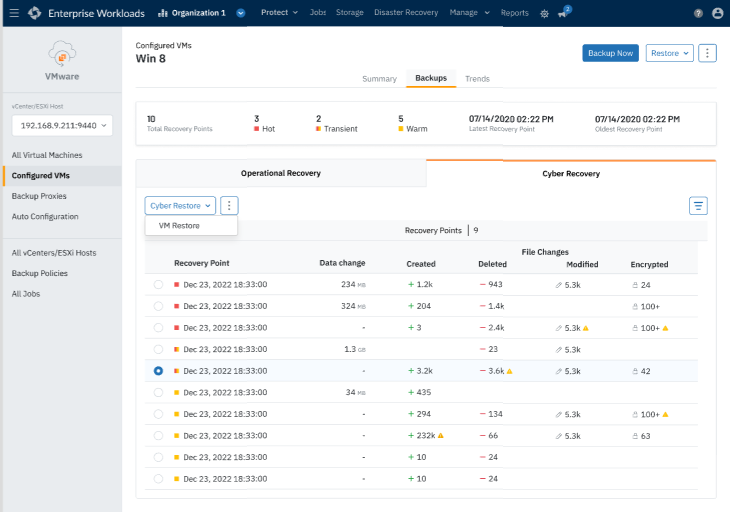
1. Data Anomaly Detection (Ingest-Time)
Automatically detects deviations in backup behavior — such as unusually large changes or unexpected deletions — which could indicate compromise or tampering. Explore Druva’s Data Anomaly Detection here.
2. Encryption Status Check (Ingest-Time)
Scans for encrypted file patterns at ingest. Useful for spotting potential ransomware-affected backups early.
3. Threat Hunt Results (At-Rest Scan)
Performs deep scans on backed-up data to uncover known Indicators of Compromise (IOCs) and latent threats using integrated threat intelligence feeds. Learn more about how to hunt threats with Druva.
4. Anti-Malware Scan During Recovery
Executes a pre-restore antivirus scan on the selected restore point. If malicious artifacts are detected, the user is alerted and can choose a safer restore point.
Each of these signals contributes to a comprehensive Recovery Posture — giving security and IT teams the confidence to proceed with recovery.