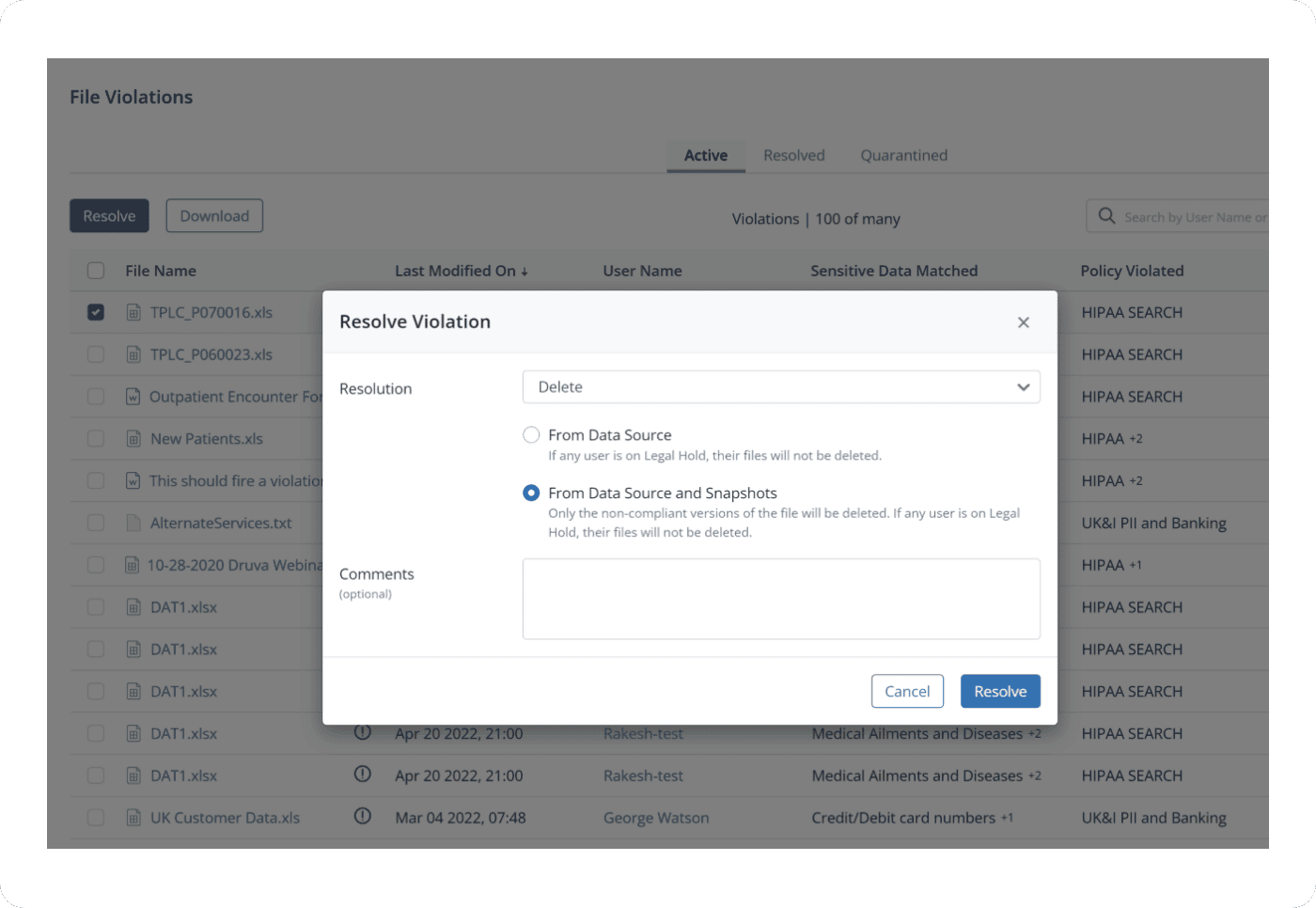
Centralized workflow resolves compliance violations per incident response policy, including deletion of non-compliant data in backup, source or both.
Benefits of cloud compliance monitoring
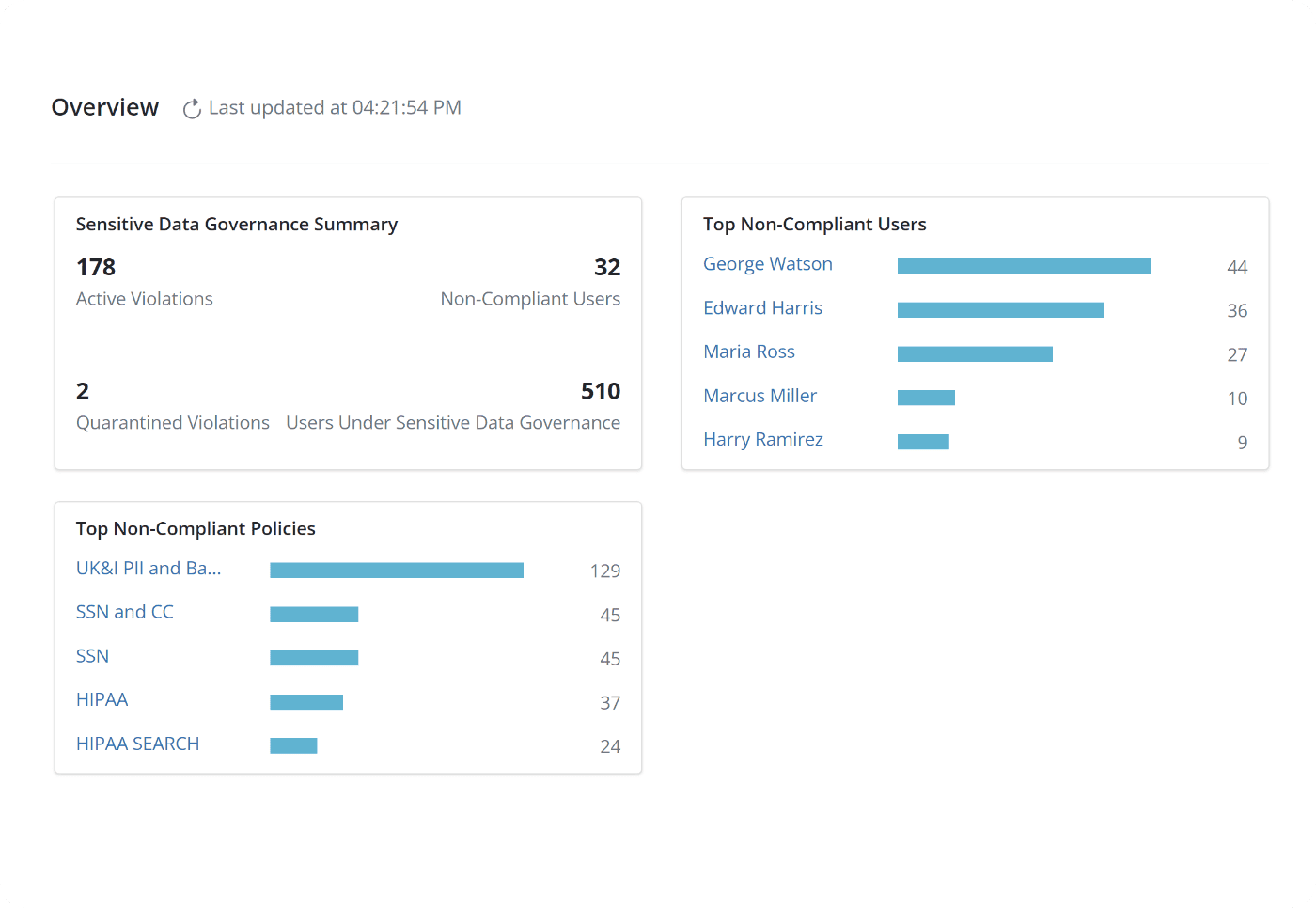
Proactively remediate risks using a compliance monitoring dashboard, with full visibility across end-user data, including Microsoft 365, Google Workspace, and endpoints.
Accelerate data compliance
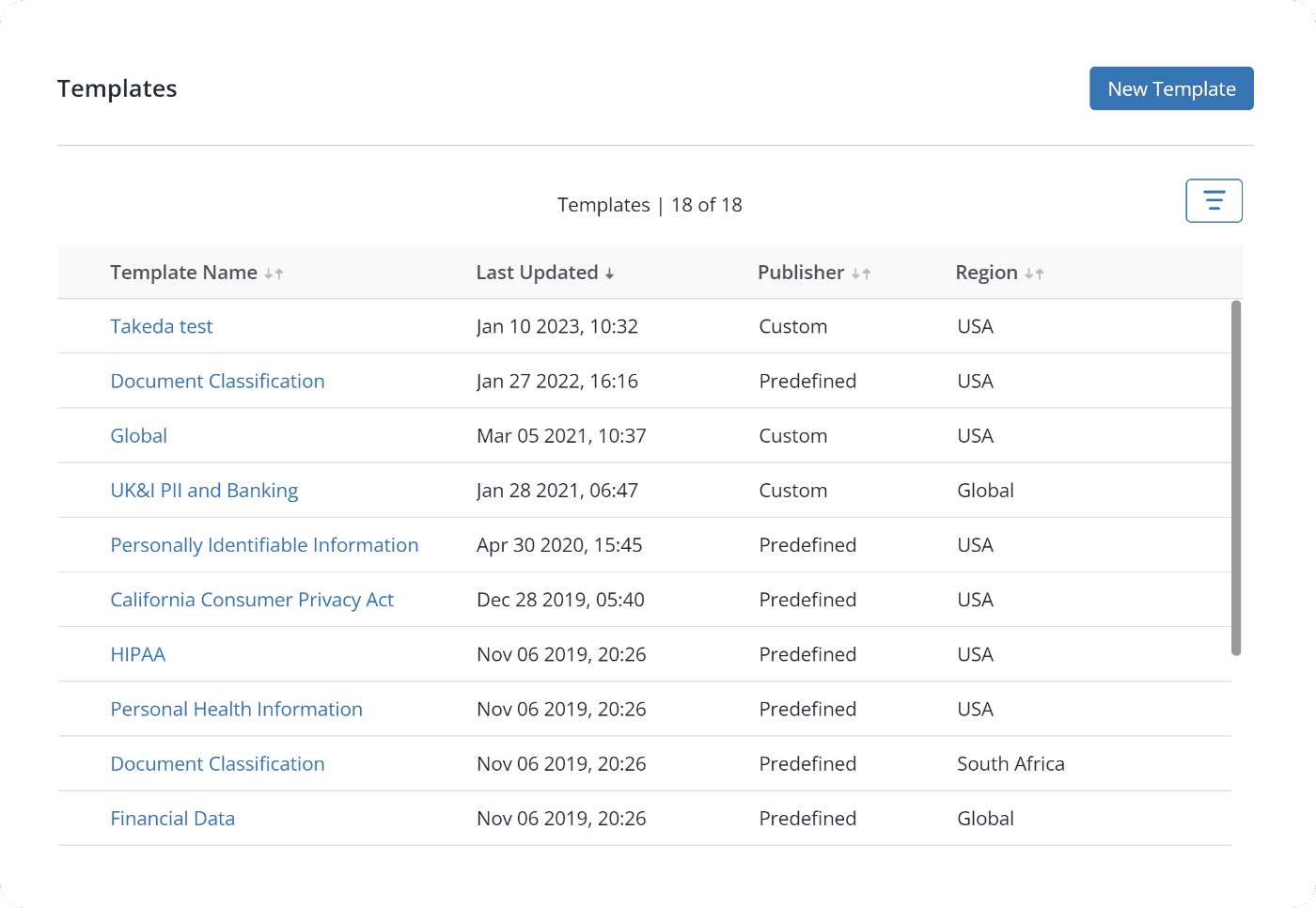
Monitor with pre-built compliance templates for key regulations, like GDPR, HIPAA or CCPA, or build your own templates, to meet your unique needs.
Proactively remediate risk
Proactively and automatically monitor data regulation compliance, across workloads, and get alerts, within 24 hours of a violation.
Rapidly respond to violations
Promptly address violations, from a single compliance dashboard, by defensibly deleting sensitive data in backup or in source, or both.
How it works
Mitigate risk with regulatory compliance monitoring that helps you comply with data regulation and governance requirements
 ×
×
 ×
×
Pre-built policy templates and rules with flexibility to customize or build your own to support regulatory or internal governance requirements.