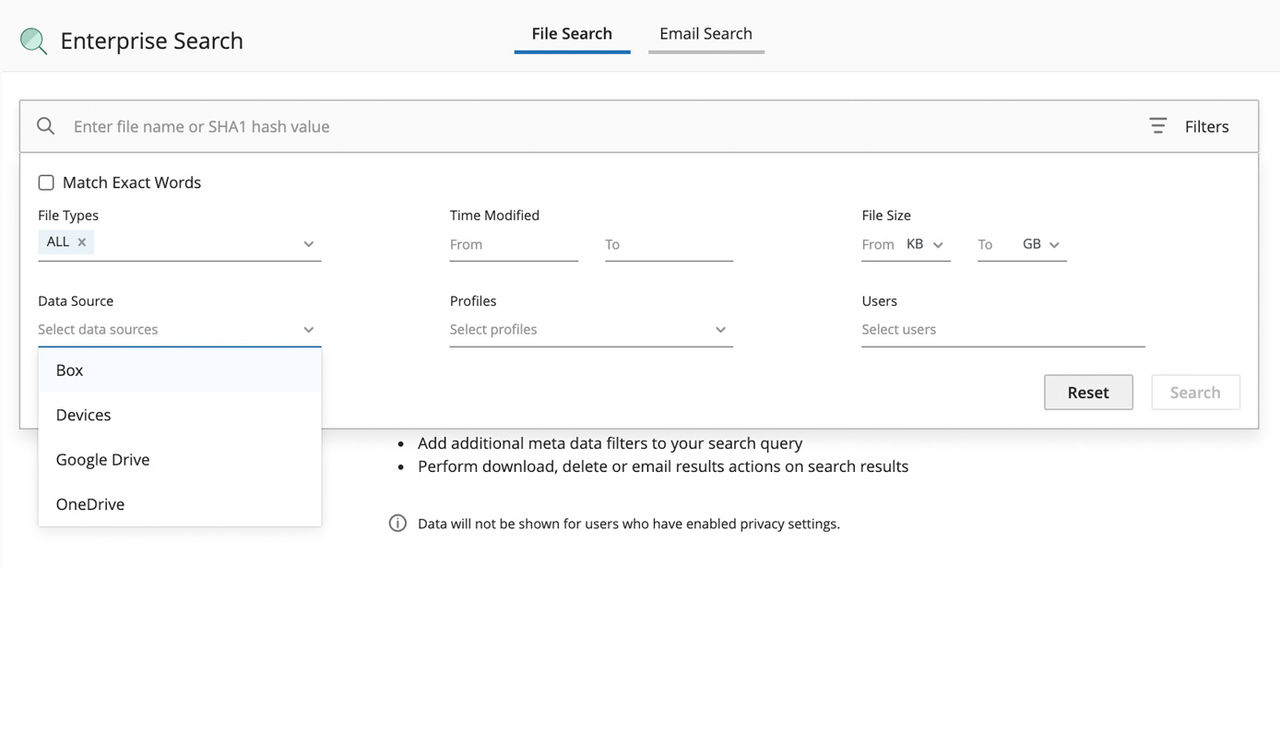
Federated (metadata) search enables IT to quickly locate files across all users, devices, and storage locations.
With Druva inSync™ endpoint backup, your data’s never lost
Integrated backup, eDiscovery and compliance monitoring. Simplify endpoint data protection, ensure regulatory compliance, and improve data visibility for the mobile workforce.
Personal Computing
Desktops | Laptops
Mobile Devices
Smartphones | Tablets
Protect Your Corporate Data Anytime, Anywhere
Combine SaaS application and endpoint backup to protect end-user data where it lives, simplifying unified search, compliance and eDiscovery.
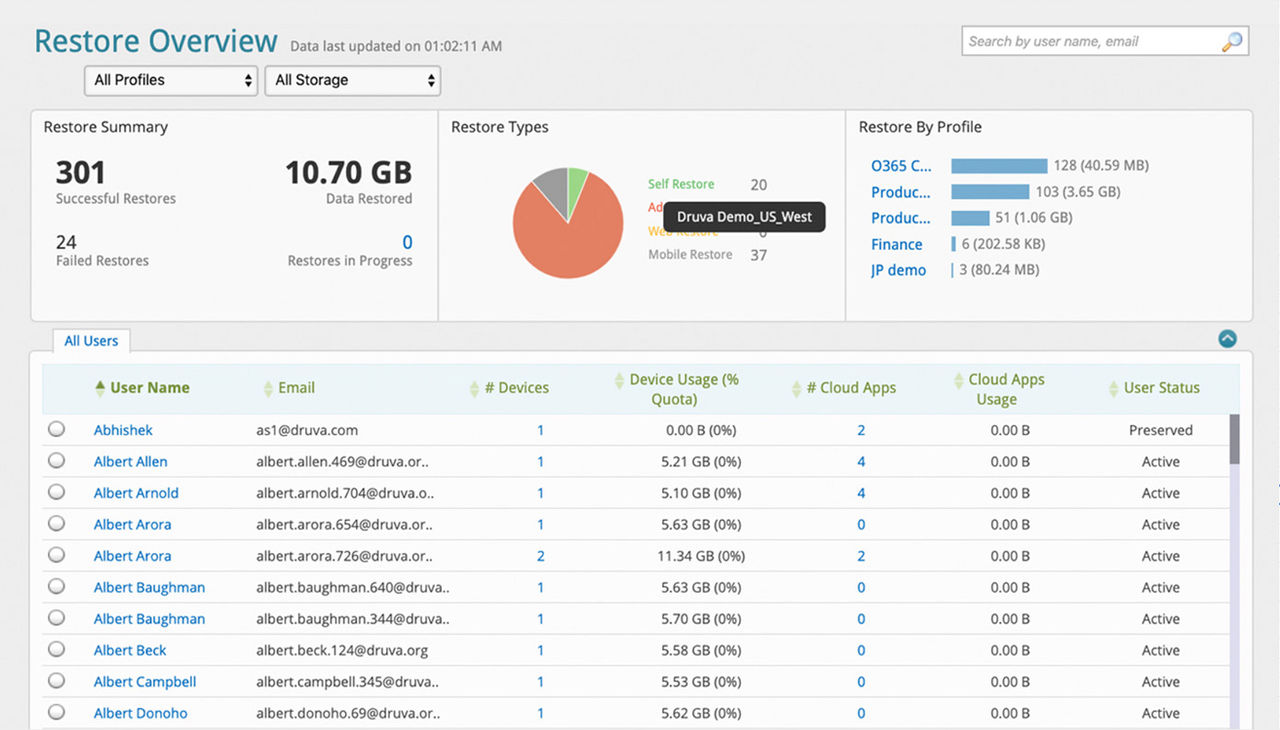
Find Your Data Quickly and Effortlessly
Reduce the time required to respond to legal hold and eDiscovery requests and leverage your centralized data for compliance and governance.
Cloud Endpoint Backup Delivered "as-a-Service"
Provision data protection within minutes, securely with on demand scalability, without the overhead of hardware, software or maintenance.
Druva Data Resiliency Cloud
Built on the Druva Cloud File System, AI-powered metadata engine, microservices-based processing, API-first, and a Zero Trust security model.
Key Features
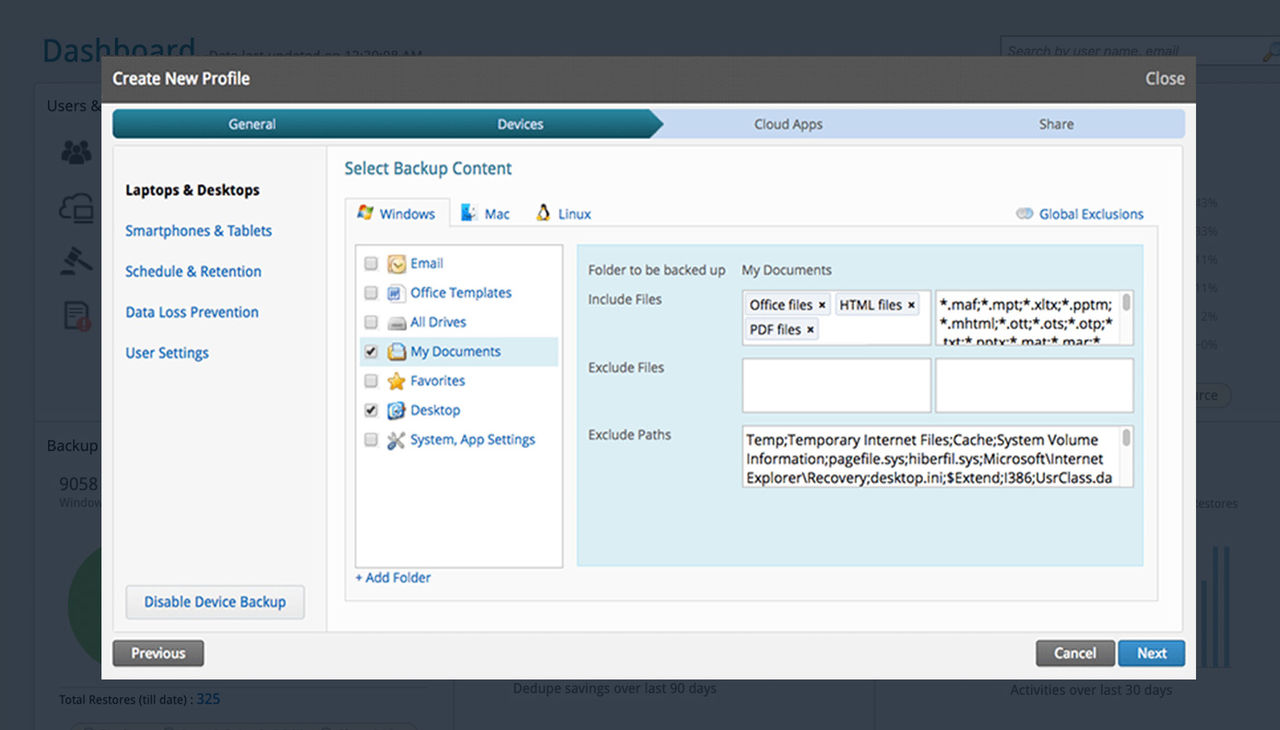
Cloud Endpoint Backup and Recovery
- Invisible backup windows (run when idle)
- End user access with self-service restore
- Global source-side deduplication
- Incremental forever backup model
Endpoint Data Management
- Data loss prevention (DLP) with remote wipe
- Fast and simple OS migration / device refresh
- Ransomware protection and recovery
Information Governance
- Federated search across all backup data
- eDiscovery enablement
- Automated & proactive compliance monitoring
Security
- Customer-only access to customer data
- 256-bit AES encryption for data at rest
- TLS 1.2 encryption for data in transit
- No key management required
- Certs: SOC-2 Type-II, HIPAA, Privacy Shield
- FedRAMP Authorized
Administration
- Cloud-based centralized management
- Role based access control (RBAC)
- Integrated mass deployment for
endpoints - MDM Integration: MobileIron, VMware AirWatch, IBM MaaS360
- Single sign-on support (SAML, ADFS)
How it Works
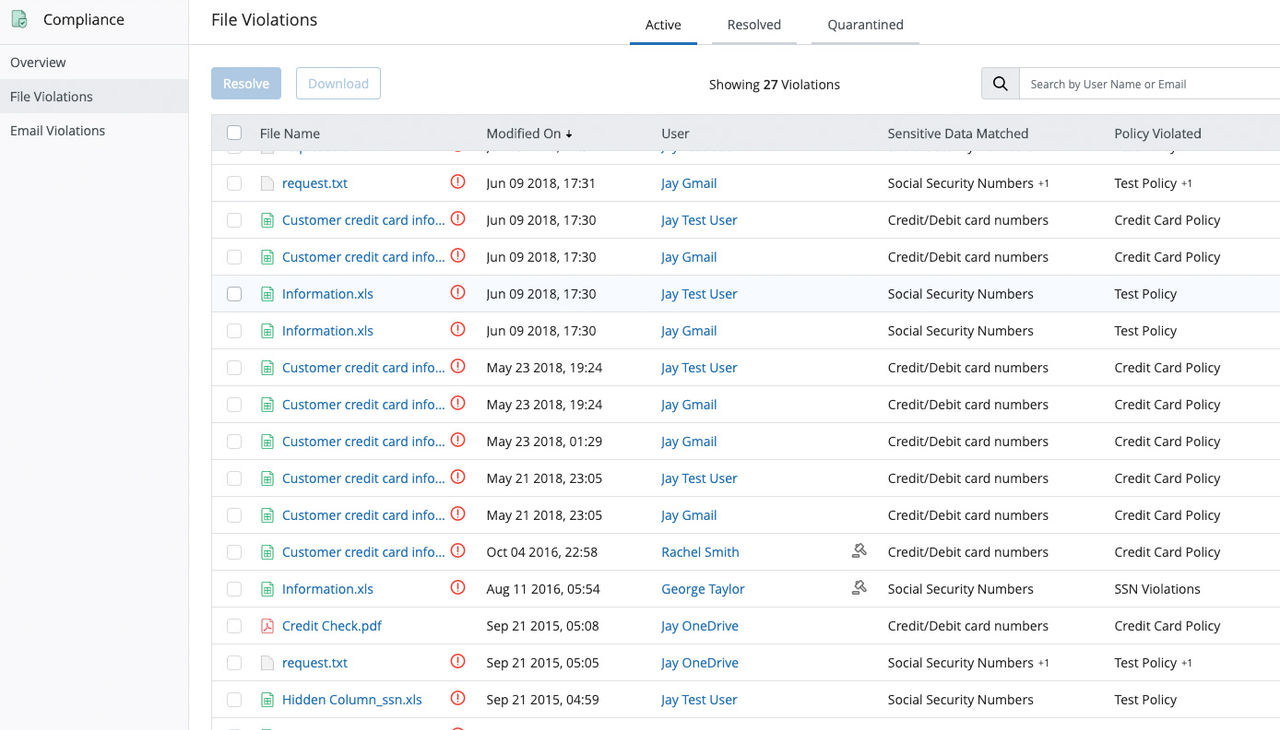
Automated compliance monitoring and management enables IT to quickly identify and remediate potential risks to at-rest sensitive data (PHI, PII, PCI).
 ×
×
 ×
×
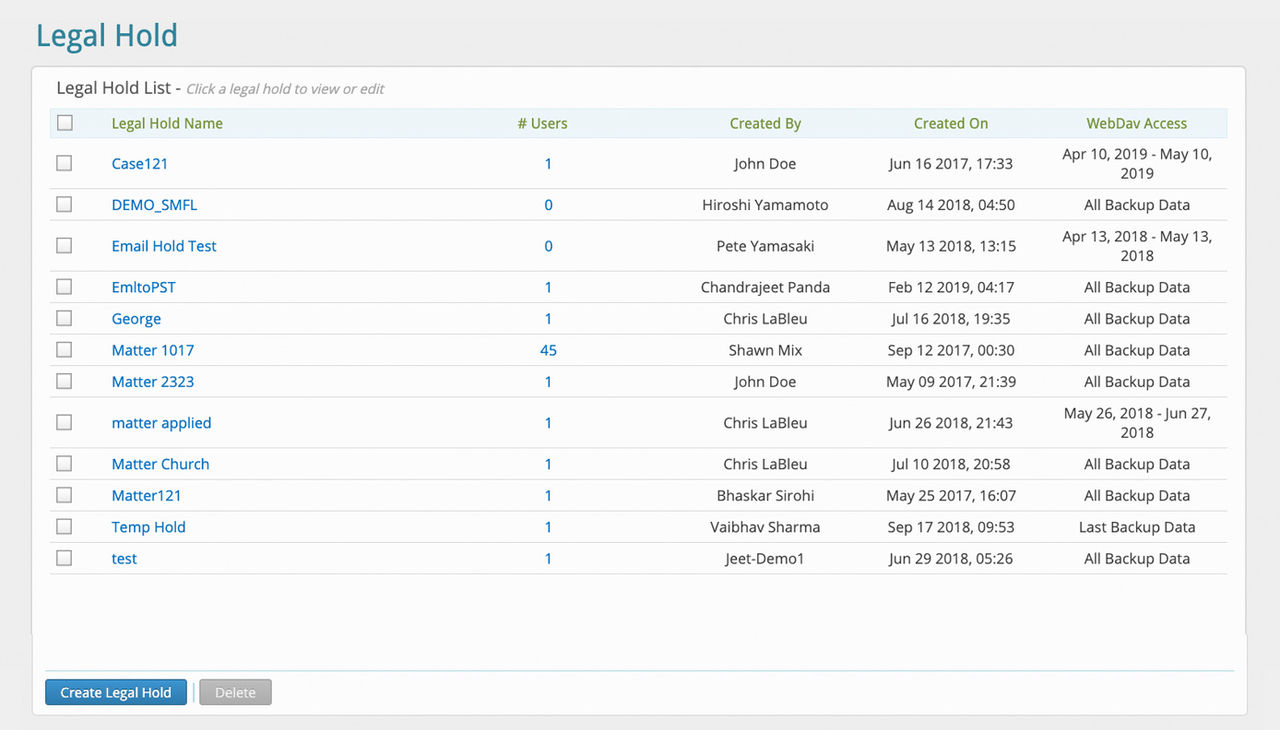
Legal hold management enables data to be preserved, maintaining chain of custody until it’s processed and analyzed in an eDiscovery platform.
 ×
×
Centralized migration management enables easy migration of end-user data and settings without interrupting business productivity.
 ×
×