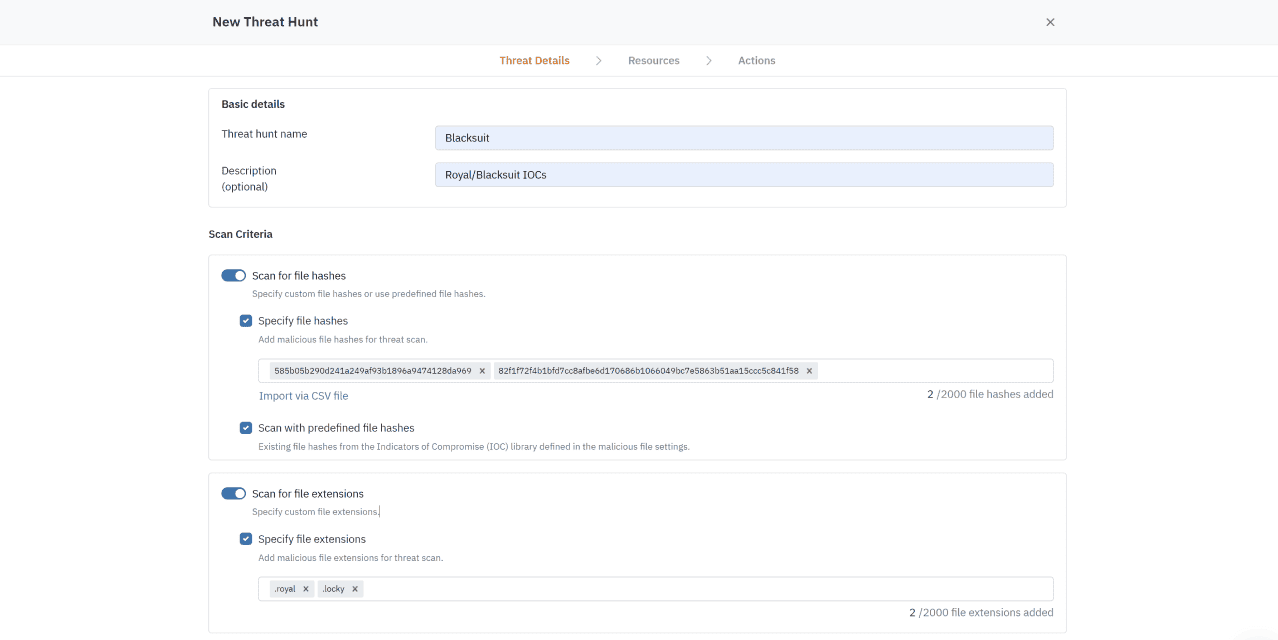
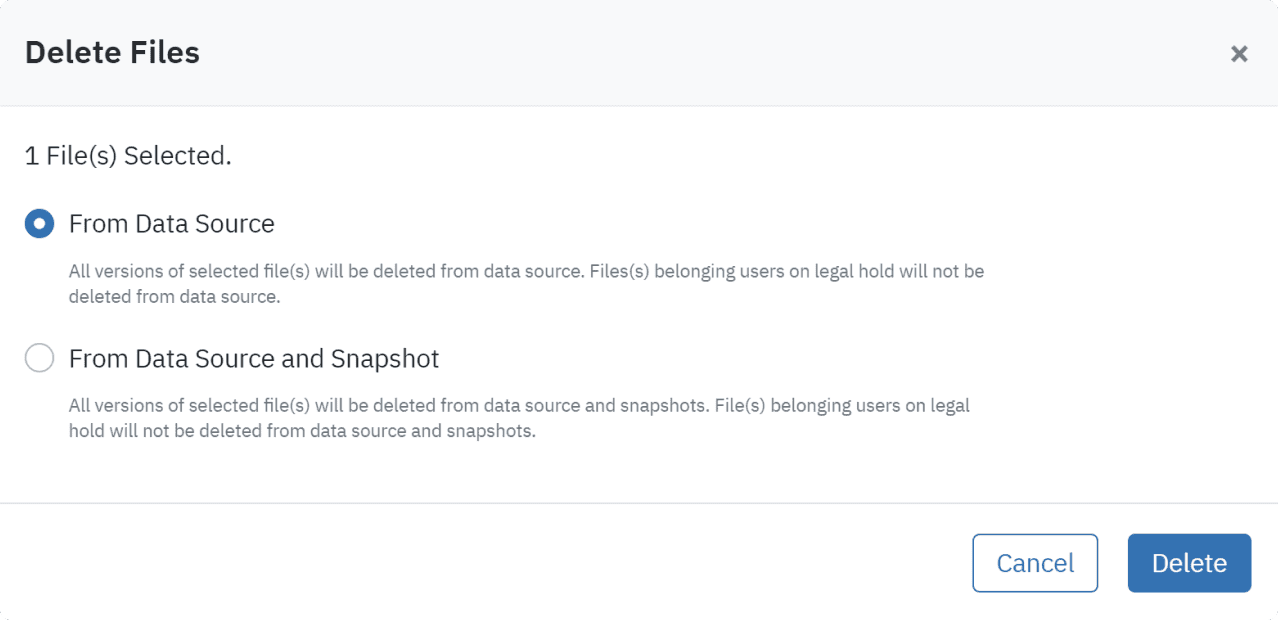
Delete infected files from backups. Receive convenient reports for auditors and cyber insurance, ensuring compliance with security processes.
 ×
×
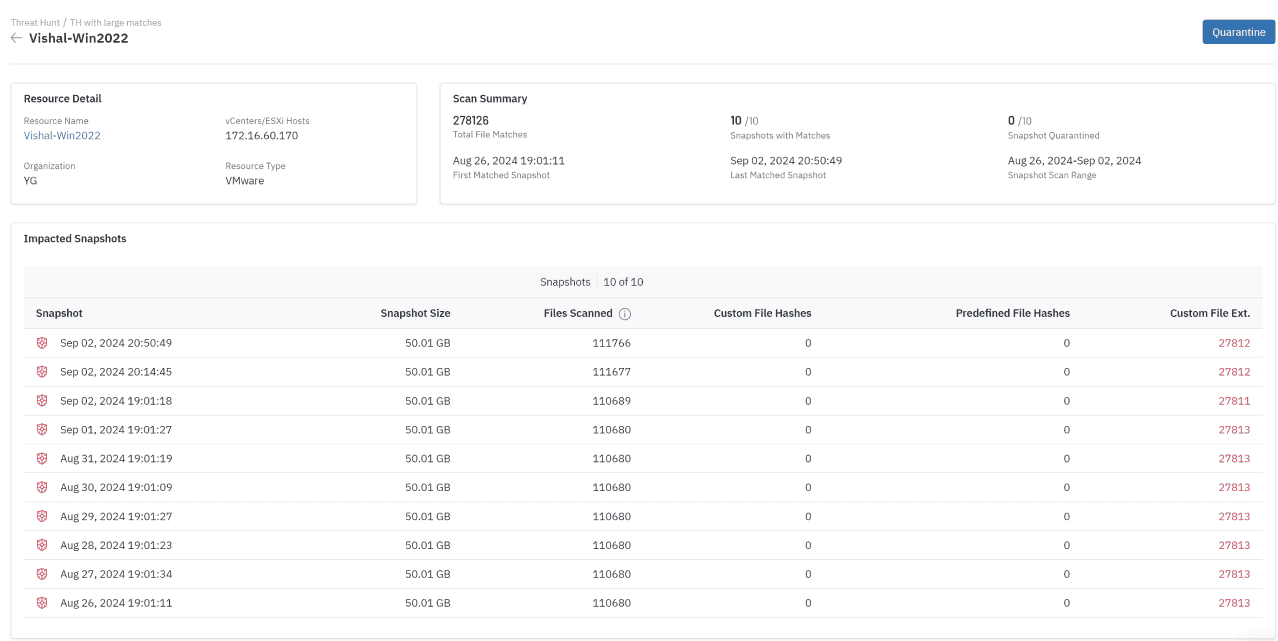
Understand scope and timeline of the attack. Contain infected files at the file and snapshot level and prevent restores that would lead to reinfection in the primary environment.
 ×
×
Accelerated Ransomware Recovery
Shorten incident response time and cyberattack recovery with automated security workflows and integrations.
Security Posture & Observability
Get real-time insights into your data security and how your environment has changed over time. Fortify your backups with these enhanced security insights.
Managed Data Detection & Response
24x7 security monitoring of backups, expert analysis, and support for threat monitoring, investigation, response, and cyber recovery.
Trusted by the world’s leading organizations