The news is full of high-profile data breach incidents: Target, Coca Cola, AT&T, Snowden. A wide range of data breach incidents that cost these organizations millions and made them media targets. And data breach is a pervasive issue; in 2011, $48 billion was lost due to data breaches in the US alone (our security breaches infographic breaks down these breaches by industry and cause). There is a lot to learn from each high-profile data breach story, but given the variety of situations, choosing the right practices and tools to prevent data breach can seem like a stab in the dark.
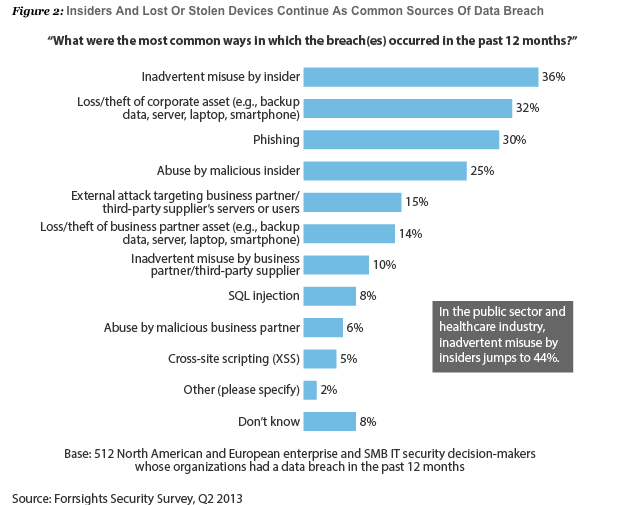
A good place to start, though, is recent research from Forrester that reveals the top 6 common ways that data breach occurs, which account for the majority of incidents. Inadvertent misuse by insiders and loss/theft of corporate assets top the list, showing that often, it’s not malicious activity that results in breach.