When I worked as a technology analyst, one of the questions that used to come up frequently in customer conversations was — what tools can we deploy to secure our enterprise perimeter? A few years down the road, the conversation has moved to a slightly different topic — how do we secure our cloud data?
My answer is, surprisingly, still the same. You can deploy a hundred security tools and still have a data breach. Just take Microsoft 365’s native security features for example. They are nothing short of impressive. A wide range of tools that span across OS, applications, endpoints/devices, identity, authentication, and data. Yet, as we discussed in part one of this blog series, the service is one of the most attacked and most breached.
If I can modify a quote from a prominent CISO — data security is more than a matter of IT. In the modern era of cloud computing, your data is dynamic, constantly moving around, shared, and flowing in and out of your organization. So, in all likelihood, there is always a chance that your data is likely to be breached. It is not a question of if but when.
What should organizations focus on?
As we are talking about Microsoft 365, let us look at the two native options that customers have for protecting their critical data — data classification and protection, or what is popularly referred to as Data Loss Prevention (DLP), and Advanced Threat Protection (ATP), which offers a combination of rule-based and a smattering of machine learning tools to protect data residing in your Exchange Online, SharePoint, OneDrive, or Teams. from inbound attacks.
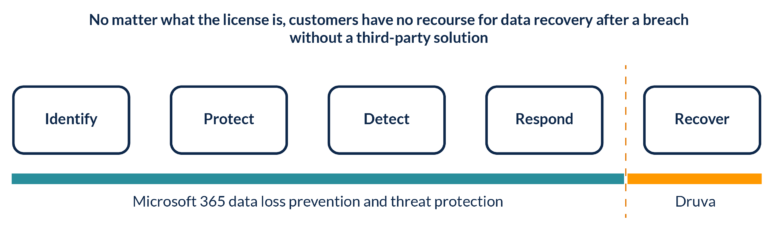
Neither of these is new, nor were they designed for the cloud. They originated from the days when Microsoft predominantly operated behind a firewall and have been repurposed to fit the cloud environment. Circling back to the earlier question of foolproof protection, there are enough examples out there to demonstrate that these are not. So what is missing in Microsoft 365 data protection?
No guarantees for data recovery
One of the common misconceptions among Microsoft 365 customers is that Microsoft is responsible for protecting their data in the event of a breach. I invite them to go through the Microsoft SLAs for each of the applications that make up the Microsoft 365 service. You will notice that the SLA and the service credit clauses are centered around service availability and not for data loss in the event of a breach or accidental deletions. More interesting still, Microsoft does not offer any recourse to recovering your lost data. So, a key question that organizations need to ask themselves is, “If I lose my data, is there a way to recover it?”