Reduces human errors
During a cyber threat, mistakes can be costly. As automation ensures most of the workflow is completed, humans can focus solely on the critical pieces that require their attention.
Promotes team collaboration
Steps in an incident response playbook can span across multiple teams such as IT, data security, network operations, and so on. As the steps are intertwined, all teams must come together to understand who is responsible for which step and how their applications integrate and pass data between each other.
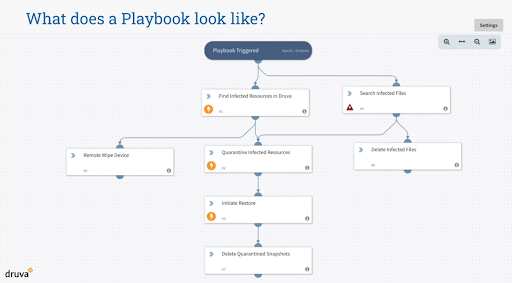
Scenarios where you can use these playbooks
Identifying a threat
Every alert that a security tool generates must be checked to identify if it’s really a threat. You can fetch information, such as the owner of the data, when the data was last backed up, or which location at which the data was accessed, using applications like Druva. This information can then be fed into a security automation tool like Cortex XSOAR from Palo Alto Networks. Once the security tool has processed the data, it can determine if it’s a real threat before initiating the next set of steps.
Containing an incident
Restricting the infection to a few data sources is a crucial step in defending against a cyber attack. Your playbook can specify how to take a device or server offline as soon as your network management tool detects anomalous network behavior.
Conducting deep forensics
You should use a playbook to pull information from several applications that can help uncover how and when you were attacked by ransomware. The playbook can consolidate this information into a CSV file and email it to stakeholders for analysis of the gaps that need to be filled.
Restoring data
After you have manually deleted the malware from the infected data, you can use a playbook to automatically restore all quarantined data to its respective locations.
Can you create your own incident response playbook?
Absolutely, yes! Rishi of Palo Alto Networks mentions that Cortex XSOAR, a security automation tool, has several use case-specific sample playbooks available for use. However, if you want to make changes to the playbook to suit your organization’s requirements, you have the flexibility to customize it per your needs and protocols.
You can also combine steps from multiple sample playbooks to build your own custom playbook.
Similarly, some of the applications that you already use today might also have their own playbooks you can explore. Rishi believes that Druva’s app in the Cortex XSOAR marketplace can be a good starting point for organizations looking to defend themselves against ransomware.
Watch this 15 minute video where he talks to Prem Ananthakrishnan, VP Product at Druva, on creating playbooks and their value to today’s organizations. And watch Druva’s Cyber Resilience Virtual Summit 2021, now available on demand. In eight 10-15 minute sessions, security leaders, Druva experts, and industry peers discuss how to ensure ransomware is no more than a minor inconvenience. When your data is taken hostage, you need the right people on your team to get it back with confidence.
What does the future hold?
Rishi believes that we are at the beginning of the security automation space. As time progresses, he thinks that along with Druva, Cortex XSOAR can address far more advanced use cases, such as:
- Forensics
- Timeseries analysis
- Recovery orchestration
- Insider threat management
Learn more about how The Druva Data Resiliency Cloud ensures data integrity with air-gapped, truly immutable backups that make it impossible for ransomware to execute in your backup environment.