In the previous blog post, we introduced why Amazon S3 can be used to store sensitive data to satisfy an organization’s security and compliance needs. In this first of the five-part series, we will discuss how to use Amazon S3 for data archival. We will walk you through the various Amazon S3 features like:
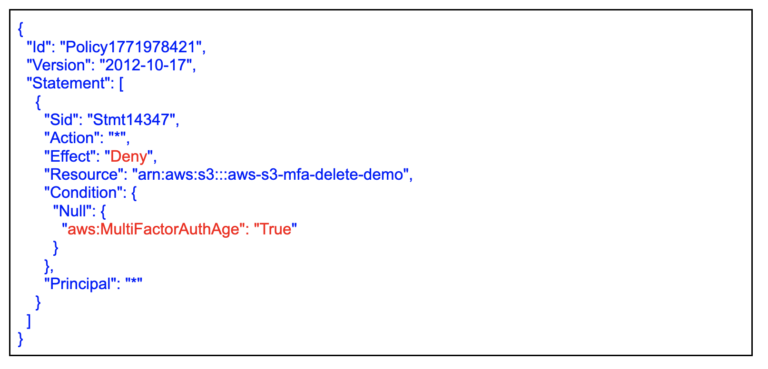
- Amazon S3 versioning and MFA delete
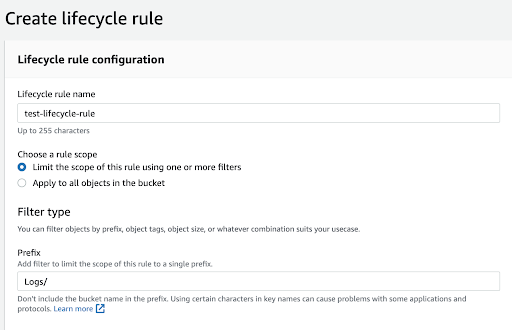
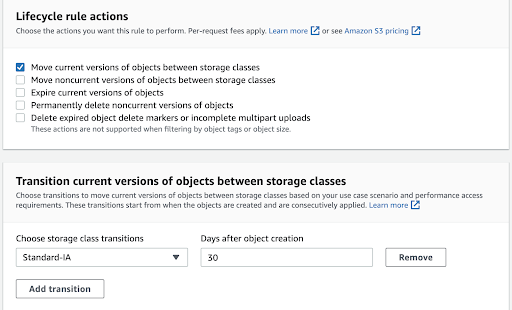
- Amazon S3 lifecycle policy
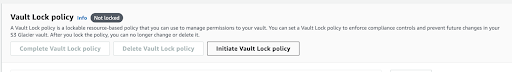
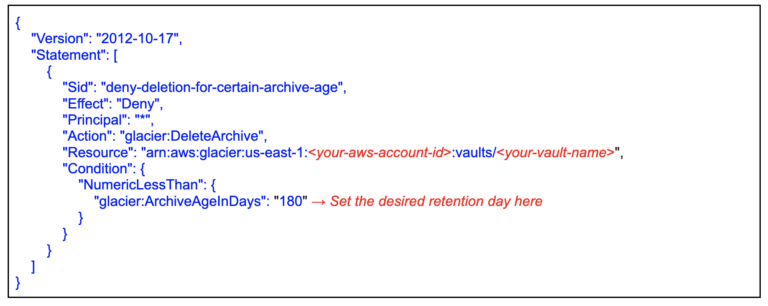
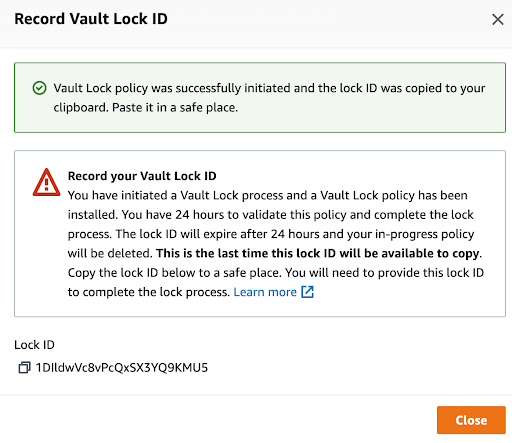
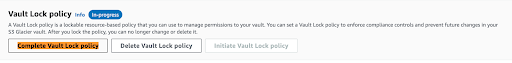
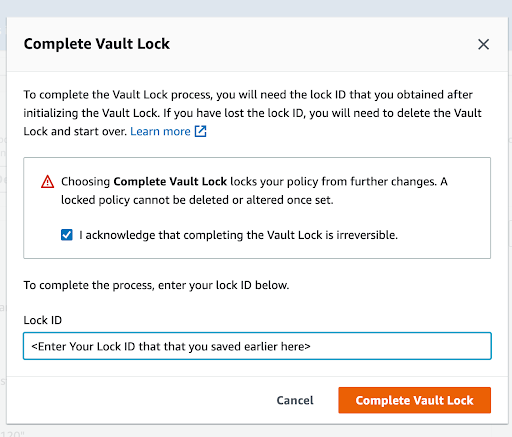
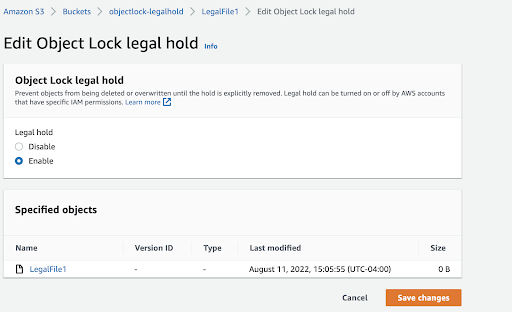
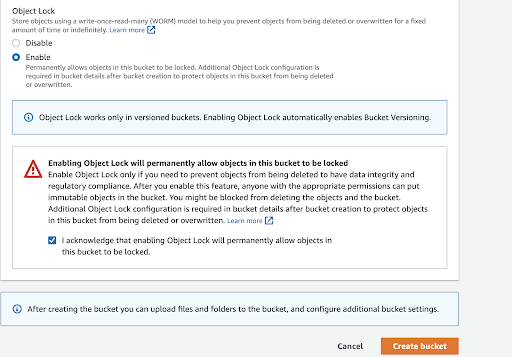
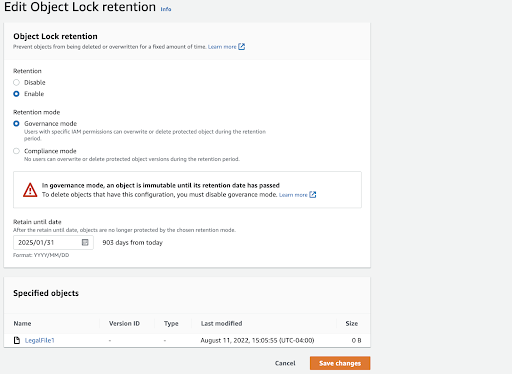
- Amazon S3 write-once-read-many (WORM)- (using Amazon S3 Glacier Vault Lock, Amazon S3 Object Lock, etc).
Amazon S3 versioning
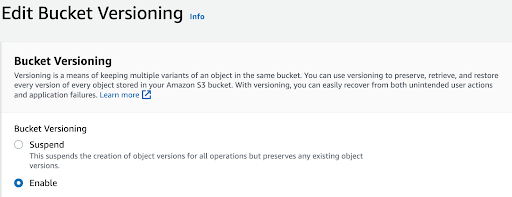
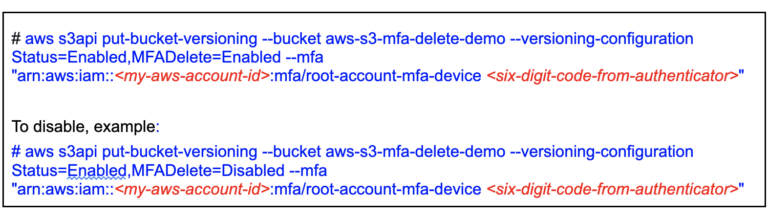
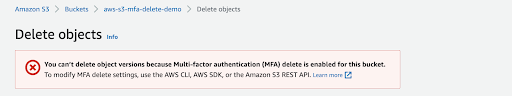
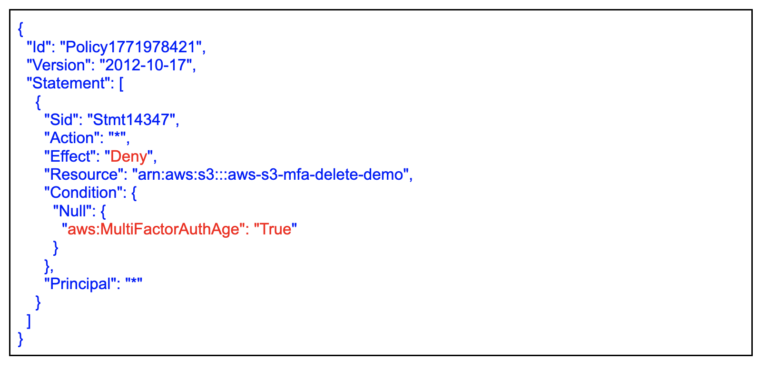
Amazon S3 versioning allows you to keep multiple versions of an object in the same bucket, allowing you to preserve, retrieve, and restore every version of every object stored in your buckets and can help you recover objects from accidental deletion or overwriting. By default, Amazon S3 versioning is disabled on buckets, and you must explicitly enable it. To enable or disable versioning on an Amazon S3 bucket:
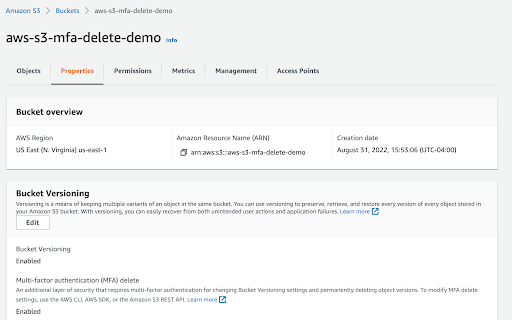
First, sign into the AWS management console and go to the Amazon S3 console. In the Buckets list, choose the name of the bucket that you want to enable versioning for. Next, select Properties. For example: