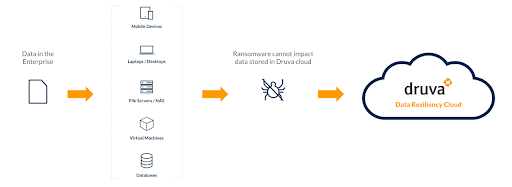
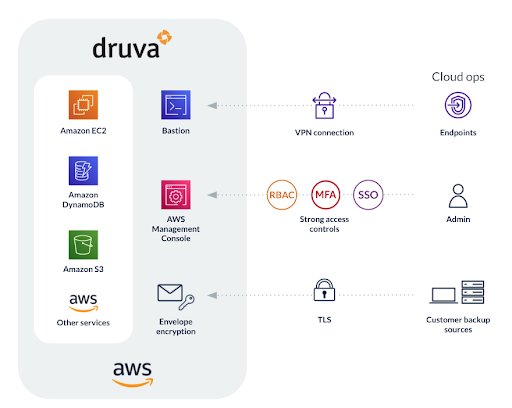
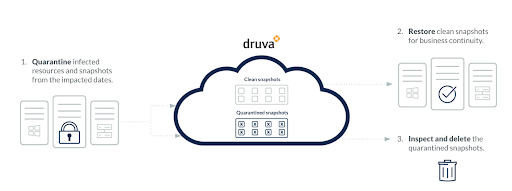
4) Identify anomalous data and activities
Once you’ve quarantined affected resources, you need to understand what went wrong during the attack. There are two levels of information that are useful in this process: access insights and unusual data activity.
- Access insights — Situational awareness of activity in your backup environment can help you identify malicious actions such as unauthorized access or deletions. Druva’s Access Insights make it easy to see which users and APIs accessed the backup environment, where the attempts took place geographically, when they took place, and what actions were attempted.
- Unusual data activity (UDA) — Ransomware attacks also produce anomalies at the data level. Quickly identifying anomalous data sets can help you choose a course of action during the recovery process and even support detection of ransomware attacks. Druva’s UDA algorithm uses machine learning to understand norms for your specific backup environment and provides automated alerts for unusual data activity including bulk deletion and encryption. You can use these insights to quickly identify affected snapshots during recovery.
5) Automate the recovery of complete and clean data
After containing an attack and understanding its impact, you are ready to begin the process of actually restoring data.
As ransomware encrypts data slowly over time, recovery is a complicated experience. The average dwell time for ransomware is dropping, but is still over 20 days, making it unlikely that the most recent unencrypted version of each file or dataset will exist within a single snapshot. And with ransomware recovery, you must go through the additional step of ensuring that data is clean before restoring it to your primary environment.
These unique challenges can be addressed with the following cloud-native infrastructure and automation processes:
- Bulk restore — Following an attack, it can be challenging to recover data across all users and workloads as quickly as possible. As cost efficiency is also a critical factor, the bulk recovery of clean data is a top priority for most enterprises.
- Druva’s Curated Recovery — Druva offers a unique solution to the problem of finding and restoring the most recent unencrypted version of files or data sets after an attack. Users simply define the time period of the attack (from initial infection to the present) and Curated Recovery uses AI to automatically find the best version of every file. The solution assembles clean versions into a single “golden snapshot” for recovery.
- Restore only clean data — Restoring contaminated data can take your whole organization back to square one. That’s why it’s vital to ensure data is free of malware before recovery. Solutions like Druva enable you to automatically scan and remove infected files from snapshots, as well as wipe infected devices clean.
Key takeaways
The threat of ransomware continues to grow and evolve. Legacy solutions fail to protect backup data from encryption and deletion, are difficult to maintain, and offer limited response and recovery options. These solutions are also ill-equipped to handle ransomware recovery across workloads that span endpoints, data centers, SaaS applications, and the cloud.
You need a sound data protection strategy and a strong data resilience vendor to help you implement and manage it. Druva can ensure your backup data is safe, help operationalize security across your backup and primary environments, and accelerate the recovery process so you can get back to normal faster.
Check out Druva’s new white paper to learn more about how you can implement best practices for ransomware protection and recovery.