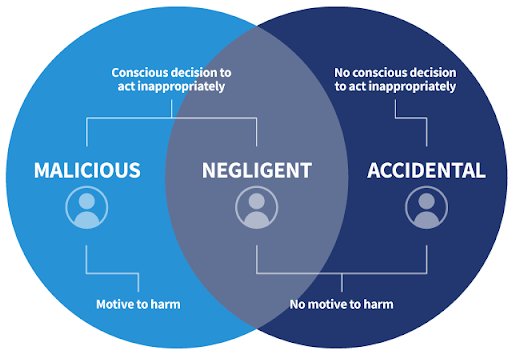
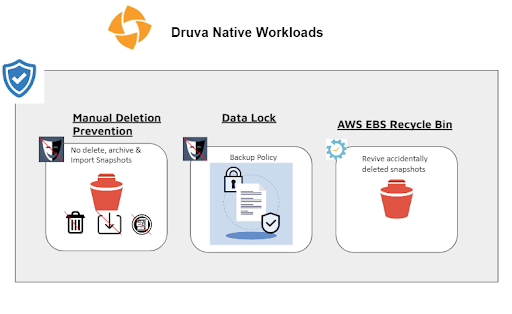
Why you should use it?
If you plan to keep a critical account safe from the manual deletion of snapshots, you can simply enable the settings for manual deletion prevention. This will give insider threats zero level of authority to play around with your data.
Who can use it?
The feature applies to enterprise and elite customers. All admins will have access and will need to raise a service desk request to enable it.
Benefits
- Zero level AWS account access in the Druva console
- Protection from insider threats
- Helps with a secured high availability AWS account
- Reduced chance of tampering in snapshots
2. Data lock
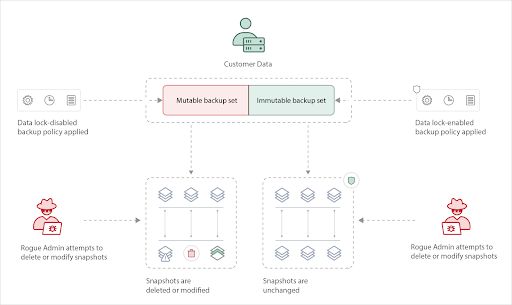
Data lock is a simple one-step feature that lets you enable a lock on the retention of snapshots created by Druva. Once a data lock is activated using a backup policy, the retention rules set on a snapshot cannot be reduced by any user.
If a policy is a data-locked policy, no matter the type of resource (EC2, EBS, RDS, EKS, DynamoDB, Redshift, etc.), it will come into effect with all resource types that Druva native workloads support. You can also view the estimated deletion date of the snapshots from the Druva console.
This enhances data security by ensuring:
- Retention on snapshots is locked to prevent tampering or deletion
- No manual archival to S3 tiers
- Zero trust security to keep important data safe
Why you should use it?
More dangerous than the actions of rogue admins are the after-effects. However, it’s simple to defend against this with Druva. If you know which backup policies need to be locked with retention on snapshots, simply enable the data lock and let the snapshot be deleted naturally after serving its expected life cycle.
Having retention-locked snapshots will help to follow the company’s strict compliance and audit checking before someone unintentionally or accidentally deletes the snapshots. You can govern these settings and disable them following a verified channel checking the authenticity of the request. You can raise a service desk ticket with Druva Support and our team would check the authenticity of the request and help with disabling the setting on the policy or required snapshots.
Who can use it?
The feature applies to enterprise and elite customers. All admins have access to the feature.
Benefits
- Helps with strict compliance and audit processes
- Quick security settings
- Protection from insider threats at the snapshot level
- Zero trust with governance
3. AWS EBS Recycle Bin
EBS snapshots are the point-in-time copy of your data and possibly the simplest way to make systems highly available and scalable in AWS. As easy as it is to manage the EBS snapshot, it is equally easy to delete a snapshot — creating potential issues for the organization. Druva’s AWS recycle bin feature covers you from accidental or intentional deletion of EBS snapshots and was recently launched at AWS re: Invent 2021.
You simply need to create retention rules on snapshots or regions from your AWS console and assign bin tags to those retention rules. Druva will discover those bin tags and allow you to add them to EBS snapshots. You can roll back a required EBS snapshot within the retention period via a single click from the Druva console.
This enhances data security by ensuring:
- Accidentally deleted EBS snapshots are recoverable
- EBS snapshots in the recycle bin can be quickly rolled back to a previous version
Why you should use it?
There can be two scenarios — first, an inexperienced user may accidentally delete an EBS snapshot needed for compliance. If it has the recycle bin tag attached, you can save this costly accident and roll back the data. Second, the effects of a malicious user targeting EBS snapshots for deletion would be prevented by bin tags on the snapshots. Admins can save the day by reviving those snapshots from the Druva console.
Who can use it?
The feature applies to enterprise and elite customers. All admins have access to the feature.
Benefits
- Easy to add bin tags
- One-click revival
- Prevents accidental deletion of EBS snapshots
Last few words
We at Druva aim to provide a best-in-class 100% SaaS product. These security features help make your life easy by increasing resilience to malicious insiders. Druva does this by enabling configurations to protect your data and snapshots from insider threats. Even if they gain access to EBS snapshots, you have another method of defense and chance to roll back from the AWS recycle bin.
Availability
We’re excited to announce that these security features—including manual deletion prevention, and AWS EBS recycle bin—are available to all elite and enterprise customers for AWS workloads today. Our Data Lock feature will be available to all elite and enterprise customers in early September 2022.
Learn more about what Druva can do for your AWS environment on the Druva website.
¹ McKinsey & Company, “How COVID-19 has pushed companies over the technology tipping point—and transformed business forever,” 5 October 2020. ² Bitdefender, “2020 Consumer Threat Lnadscape Report,” 25 March 2021. ³ Cybersecurity Ventures, “Global Cybercrime Damages Predicted To Reach $6 Trillion Annually By 2021,” 26 October 2020. ⁴ Coveware, “Ransomware Attack Vectors Shift as New Software Vulnerability Exploits Abound,” 26 April 2021. ⁵ Cybersecurity Insiders, “2022 Insider Threat Report,” 27 January 2022. ⁶ Ponemon Institute, “2020 Cost of Insider Threats Global Report,” 29 January 2020.