News/Trends
Data Compliance Made Simple in The Cloud

As the scope of regulation continues to expand, global enterprises face the daunting challenges of safeguarding data privacy, minimizing security risks, and managing the scope of data growth. While platforms like Amazon Web Services (AWS) possess both the certifications, attestations, and infrastructure to handle corporate workloads, users must be familiar with their own regulatory environment so they can use these cloud services effectively.
Taking the first step
When considering a cloud-based data solution, you’ll naturally have many questions about the security of your data. Where is your data stored? Who has access to it? Are they the same people who manage the infrastructure, and are they internal employees or vendors of the provider?
If you choose a public cloud provider, you may have additional questions about security and how that provider protects data and addresses regulatory requirements.
These questions, if left unanswered, can turn into roadblocks for your migration to the cloud. So it’s imperative that your service provider address these concerns clearly and spell them out as part of their service-level agreements. After all, your organization is ultimately liable, so it makes sense to verify that your data is compliant and secure when stored in the cloud.
A Quick Guide To Regulation
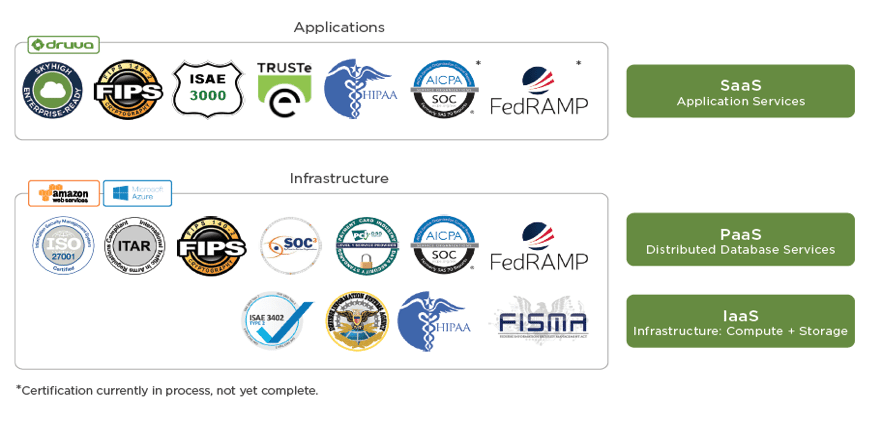
While there are many regulatory bodies and frameworks based on industry and geography, these are the ones most likely to impact your company’s use of cloud services (and the security of those services):

ISO/IEC 27001:2013 specifies the requirements for establishing, implementing, maintaining, and continually improving an information security management system within an organization. It also includes requirements for the assessment and treatment of information security risks tailored to the needs of the organization. Because the requirements set out in ISO/IEC 27001:2013 are generic and intended to be applicable to all organizations regardless of size or type, it is by far one of the most popular compliance frameworks.

Service Organization Control (SOC) is a set of accounting standards that measure the control of financial information for a service organization. SOCs are covered under both the SSAE 16 and the ISAE 3402 professional standards. While SOC 1 examines the financial reporting controls of an organization that provides services to end users, SOC 2 focuses on organizational controls based on trust-service principles that cover security, availability, processing integrity, confidentiality, and privacy. SOC 2 is a common method to evaluate security controls for cloud service providers.

The General Data Protection Regulation (GDPR) is a regulation from the EU Parliament to strengthen and unify data protection for individuals within the EU. The GDPR also addresses exportation of personal data outside the EU. The GDPR’s main objectives are to give EU citizens control of their personal data, simplify the regulatory environment, and standardize international business practices. When the GDPR takes effect in 2018, it will replace the EU Data Protection Directive originally passed in 1995.

Passed in 1996 and updated in 2009 and 2013, the Health Insurance Portability and Accountability Act (HIPAA) is US-specific legislation that provides data privacy and security provisions for safeguarding medical information. Title II of HIPAA impacts IT departments the most, as it directs the Department of Health and Human Services (HHS) to establish national standards for processing electronic healthcare transactions. It also requires healthcare organizations to implement secure electronic access to health data and to remain in compliance with privacy regulations set by HHS.

The Federal Risk and Authorization Management Program (FedRAMP) is an assessment and authorization process used to ensure security is in place when accessing cloud computing products and services. FedRAMP uses security controls outlined in the National Institute of Standards and Technology Special Publication 800-53, which were specifically selected to provide protection in cloud environments. Prior to the introduction of FedRAMP, individual government agencies would evaluate and use their own cloud service providers according to the Federal Information Security Management Act of 2002.

The Payment Card Industry Data Security Standard (PCI DSS) was created in 2004 by the four major credit-card companies. It’s a widely accepted set of policies and procedures intended to optimize the security of credit, debit, and cash card transactions and protect cardholders against misuse of their personal information. In April of 2016, PCI DSS was updated with new requirements for the use of TLS encryption, multi-factor authentication, and new service-provider requirements for change management and penetration testing.
Whether yours is a global enterprise or a governmental agency (or anything in between), organizations like yours face complex challenges: data privacy and security risks, the growth of data and the mobile workforce, and shifting privacy regulations. Druva combines complete data privacy and security with a transparent, intuitive user experience to deliver best-in-class data protection and regulatory compliance in the cloud. Learn more about security and trust.